Yagaan SAST
Yagaan SAST for VS Code retrieves and explains the results of a Yagaan (Pradeo) source code security scan, helping you quickly identify and fix vulnerabilities. This extension connects to a Pradeo Scan Server to display detected security vulnerabilities as warnings directly in your IDE. You therefore need an account on a Pradeo Scan Server, either on-premise or as a service at https://scan.yagaan.io You'll then attach your workspace to a previously scanned project (using CI pipeline for example) in order to retrieve and synchronize detected issues with your workspace. QuickstartSetting up Connection and AuthenticationFirst, configure your connection to the Scan Server in VS Code settings. We recommend using a Personal Access Token for authentication. You can generate one from your Scan Server account page 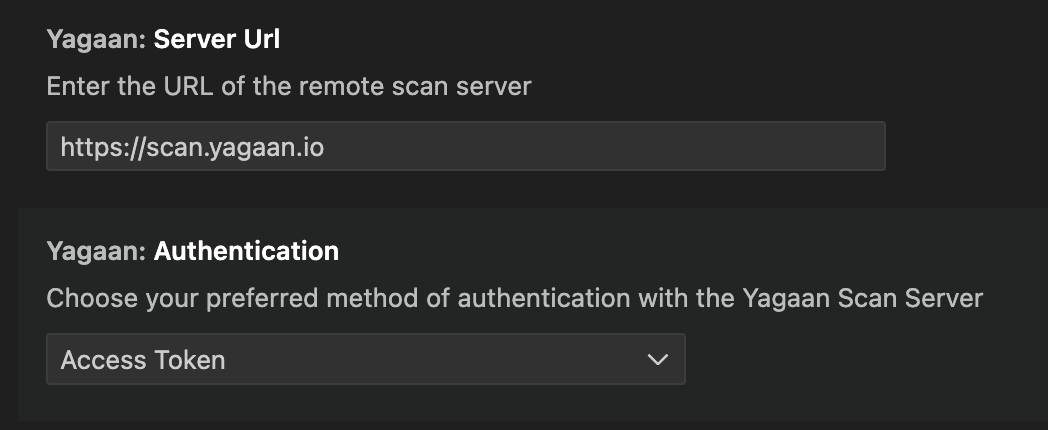
Attaching to a ProjectOnce authenticated, you can link your current workspace to a scanned project:
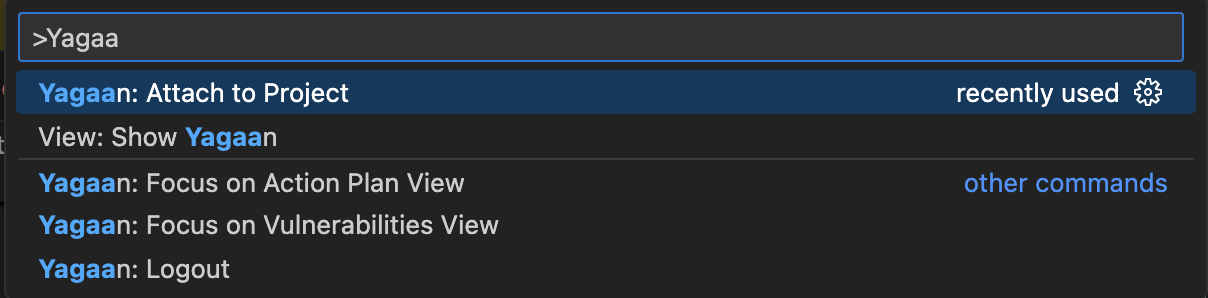
After linking, detected vulnerabilities will appear in your workspace for review. RequirementsYou need a Pradeo Scan Server, either on-premise or SaaS. See https://www.pradeo.com. FeaturesAI vulnerability explanation and chatIf a code-mining server is configured in the Yagaan plugin settings, you can access AI-generated explanations for vulnerabilities. Explanations are produced by the code-mining server and a self-hostable LLM, ensuring full privacy of your code. The deep knowledge of the code analysis provided by the code-mining enables the generation of contextual and high-quality explanations, even when using self-hosted LLM models. The explanation of each selected vulnerability will be displayed in the You can also do ai-chat with the explanation in order to clarify some points about the vulenrability or to give some additional context or insight. If you've configured a code-mining server within the Yagaan plugin settings, you can access AI-powered explanations for your code. These explanations are generated by the code-mining server and a locally hosted language model, ensuring your code remains private. You can also engage in a conversational chat about the explanation to gain further clarity, additional context, or deeper insights into the vulnerability. 💡 AI and code-ming features are optional and require a configured code-mining server. Vulnerabilies explanation and resolutionExtension help developers to understand the security issues found within their code. Each identified vulnerability is accompanied by an interactive diagnostic, detailing the nature of the issue, its causes, and its potential exploitation flow. 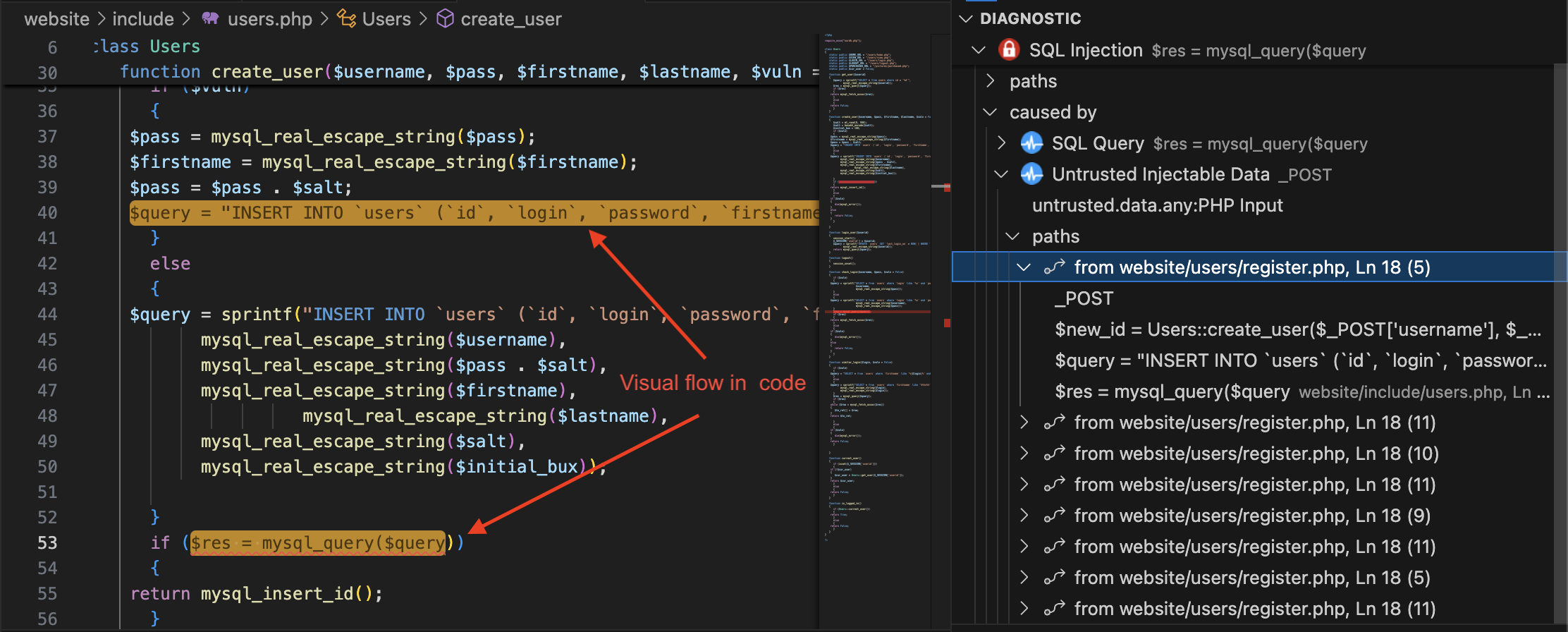
In addition to understanding the vulnerabilities, the extension provides actionable remediation guidance and some examples (if any) extracted from the scanned project itself. 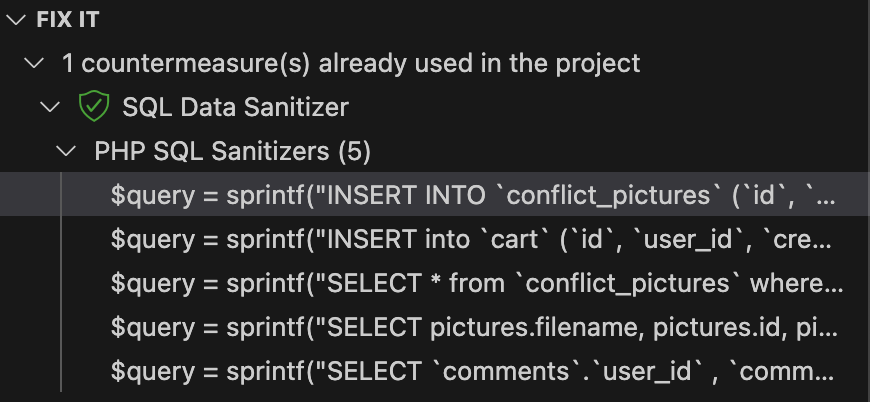
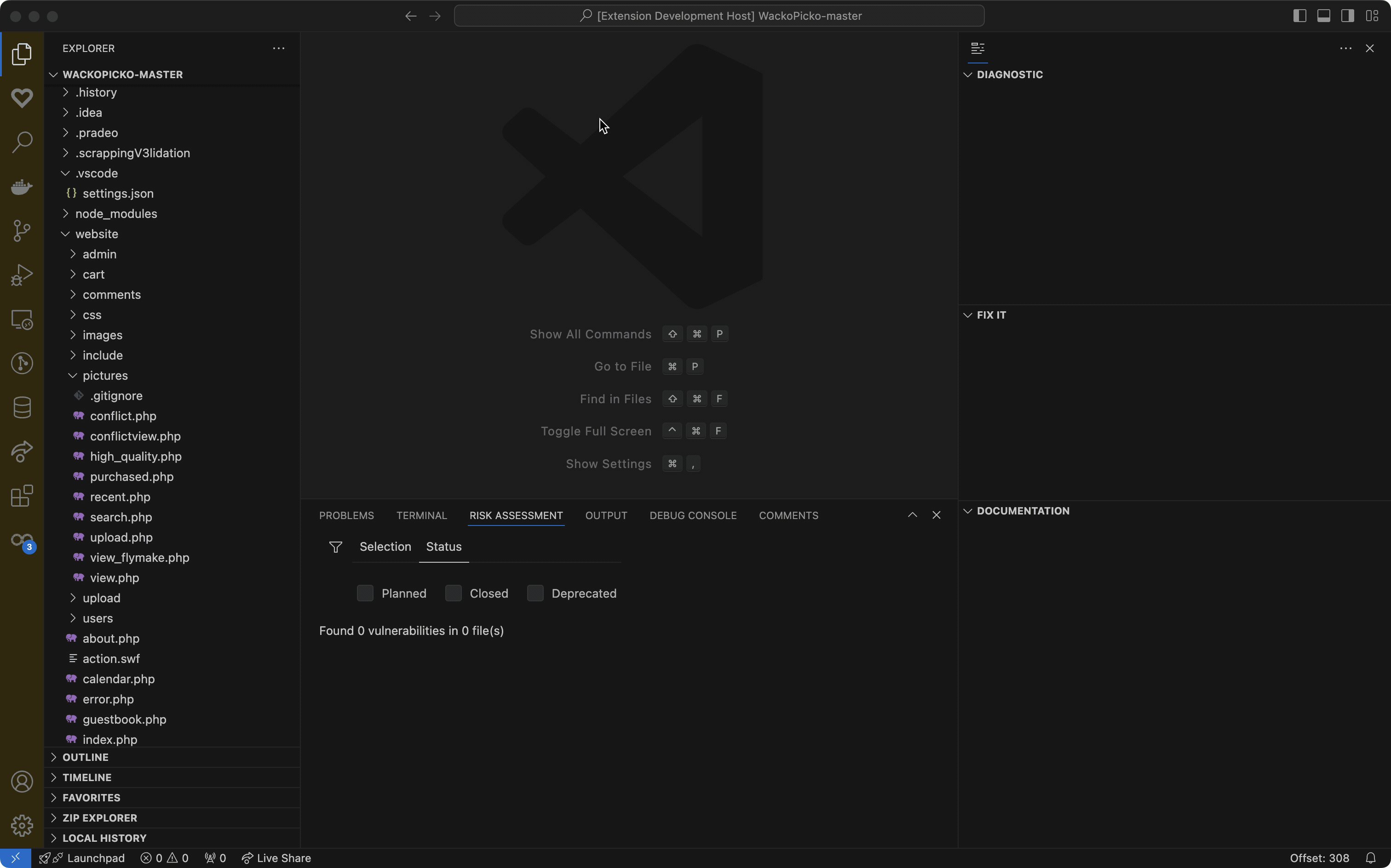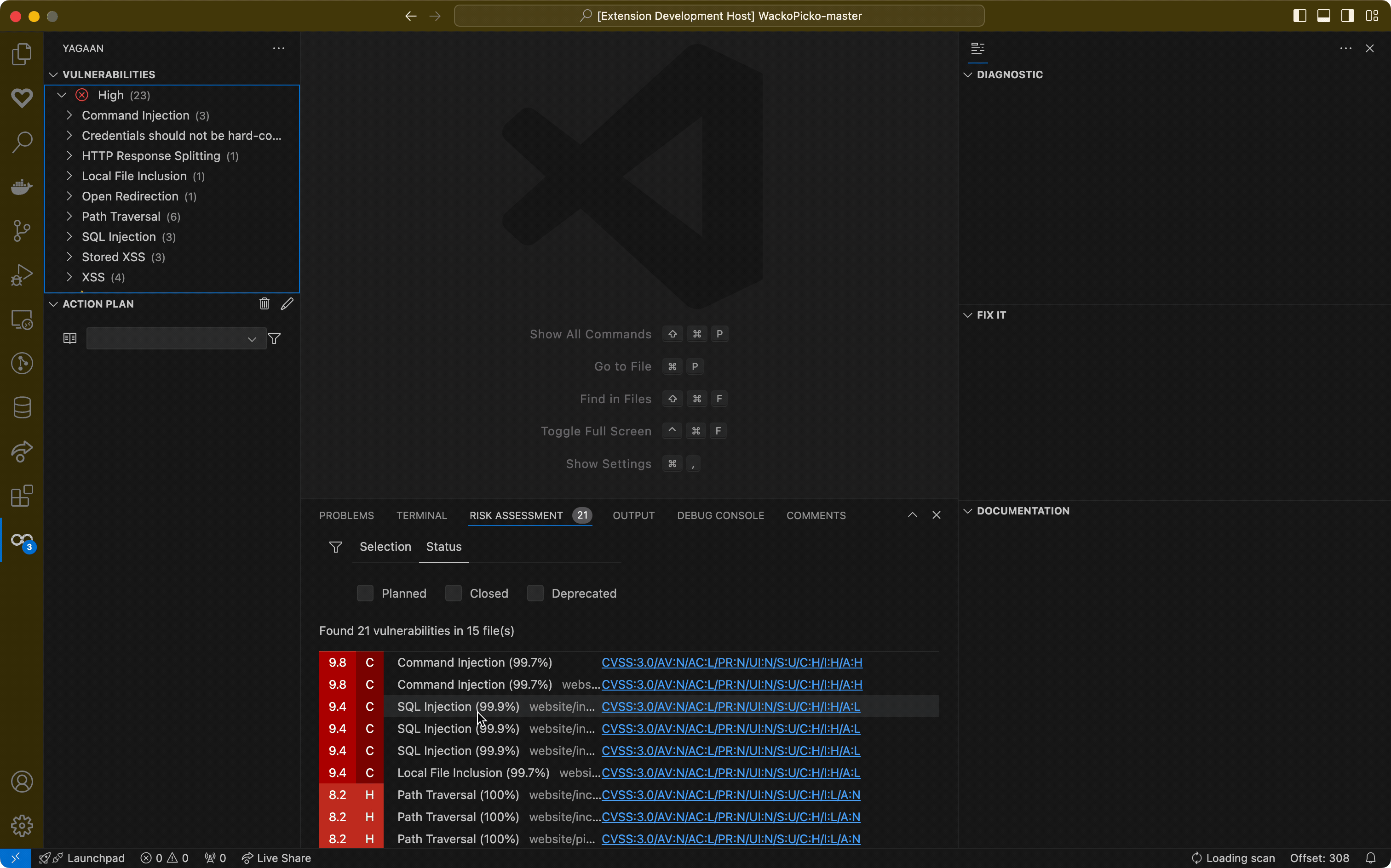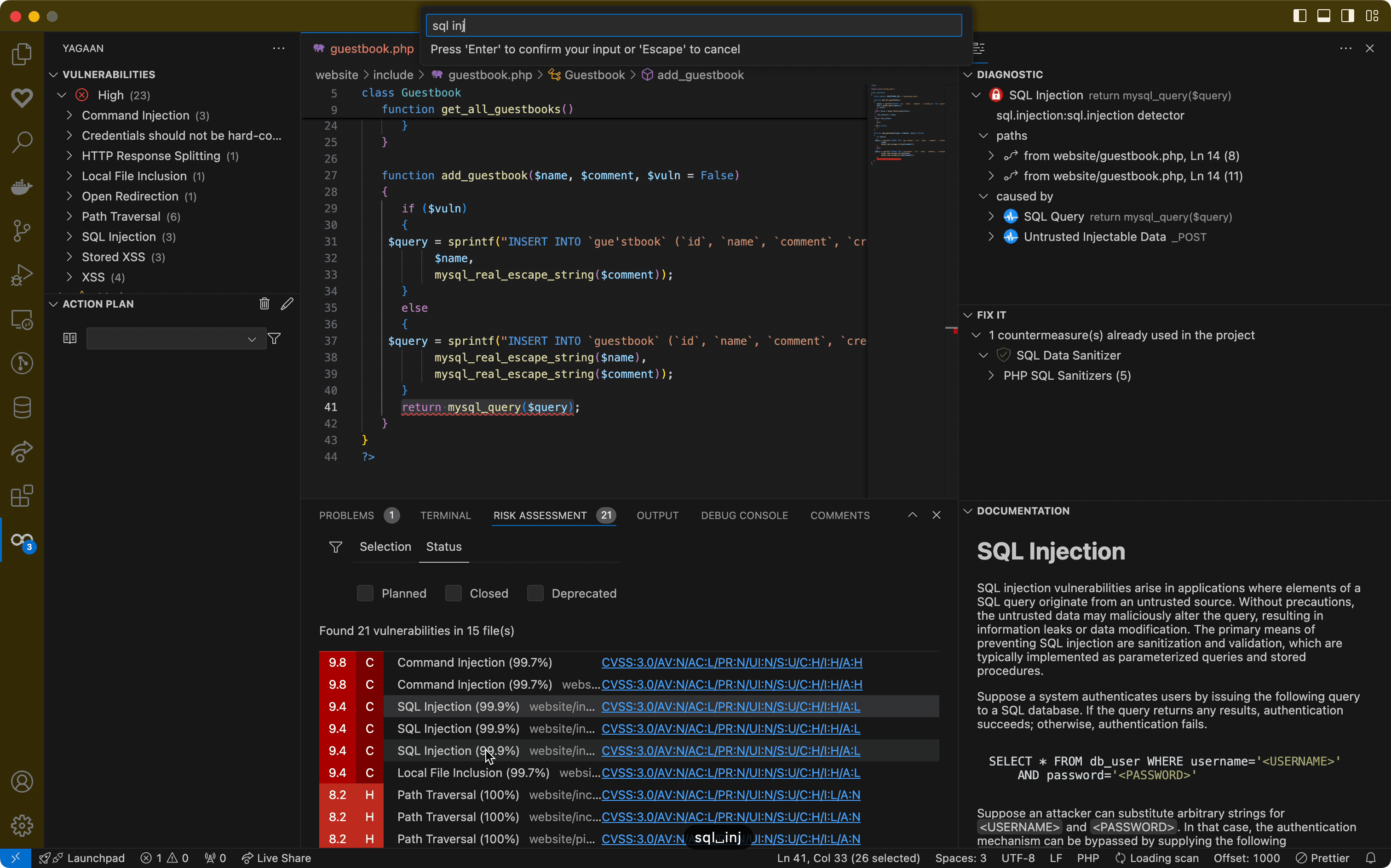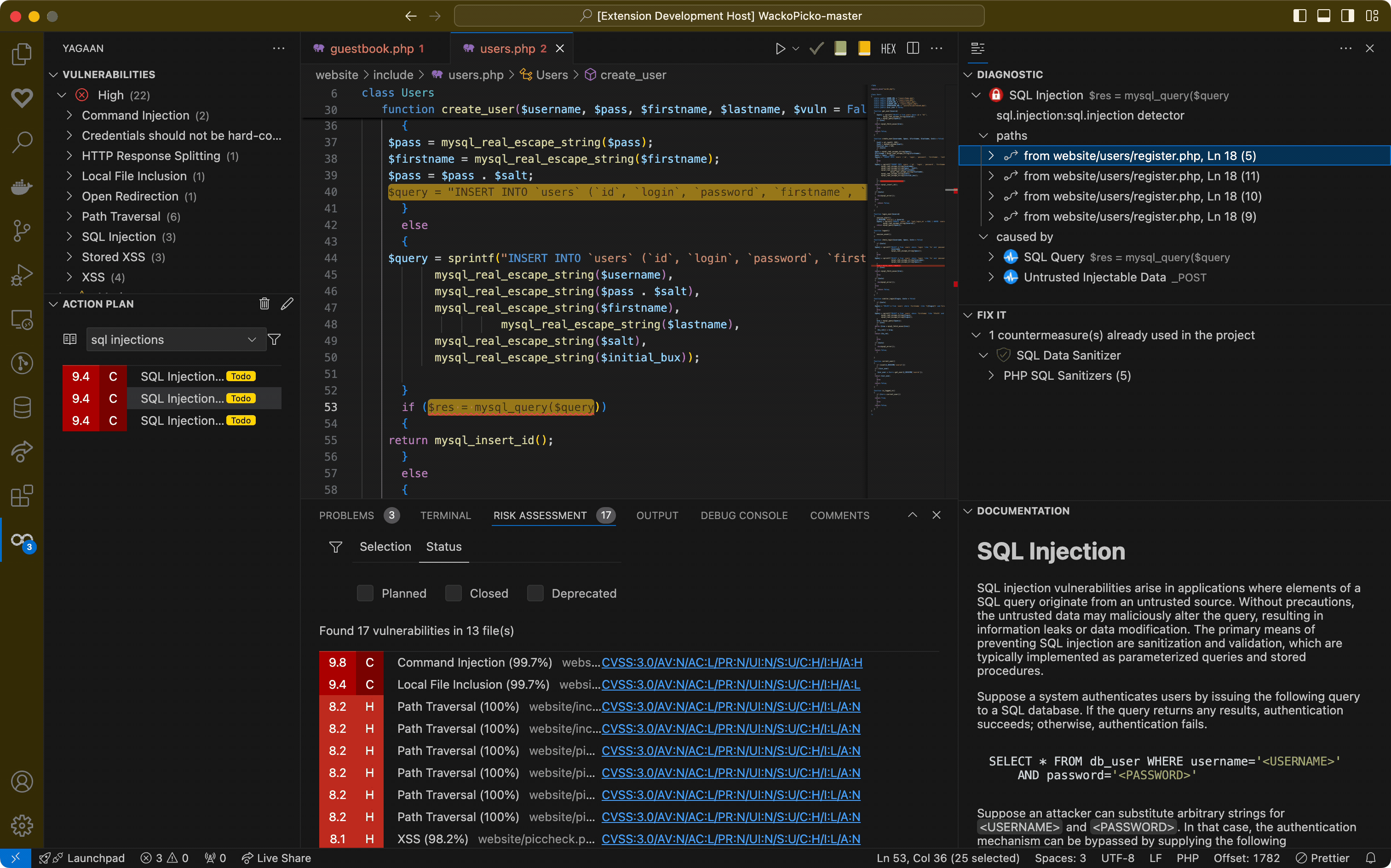
Risk assessmentThe Risk Assessment feature focuses on prioritization by evaluating each identified vulnerability based on factors such as severity, exploitability, and potential impact on your application and its users. This assessment assigns a CVSS score to each vulnerability, allowing developers to quickly identify which issues require immediate attention and which can be scheduled for future fixes. 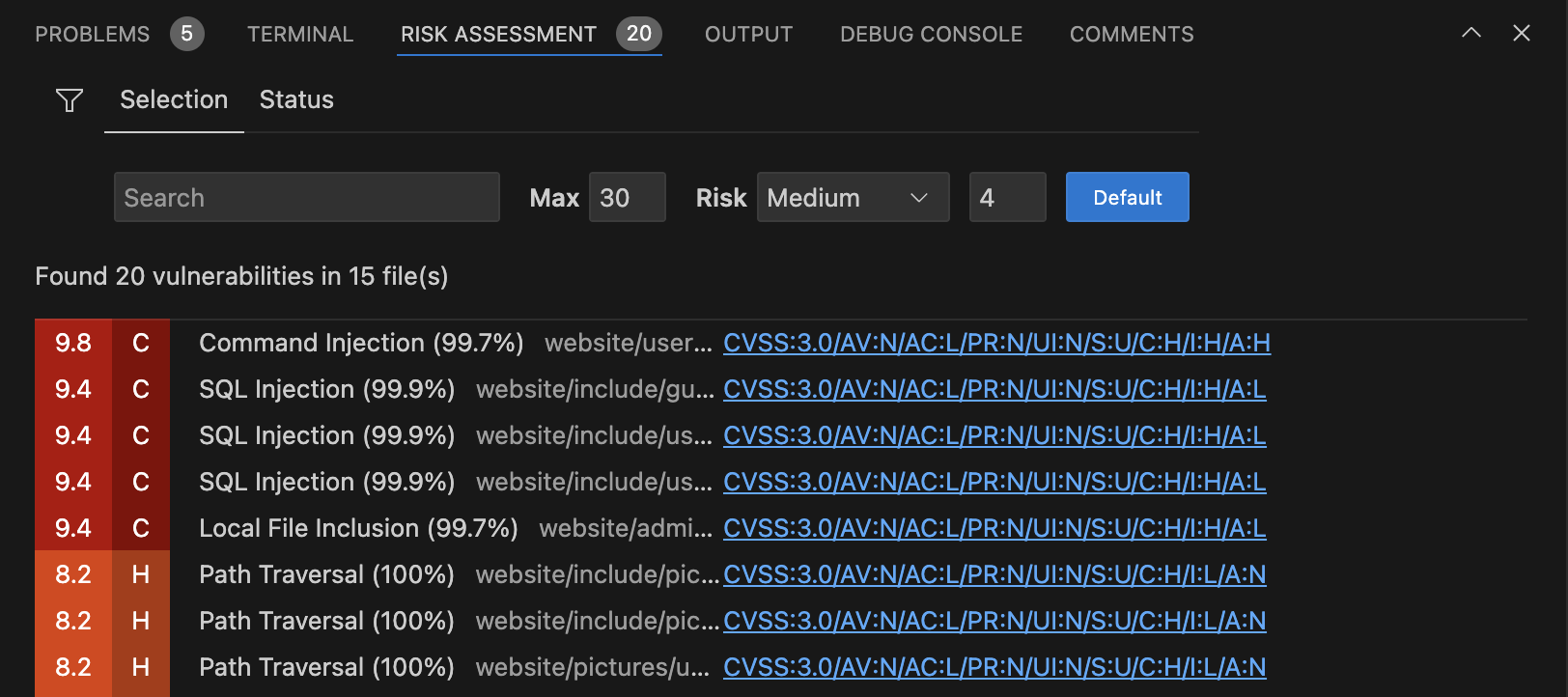
Action planThe Risk Assessment view lets you create a straightforward action plan that all developers with access to the project's scan can share. 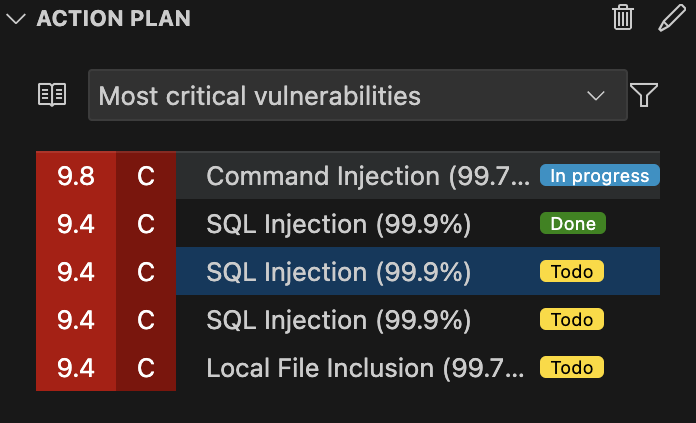
By having a clear list of prioritized vulnerabilities to work on, the team can focus their efforts together on the most critical risks, making it easier to boost the project's security while working as a team. Status of a vulnerabilityEach vulnerability has a status which is obtained from its potential action plan and of the current workspace state:
You can use those status to filter the risk assessment view:
Create an action planBefore creating an action plan, ensure you've already attached your workspace to a project on the Pradeo Scan Server. To create an action plan:
The plan will appear in a dedicated view and be shared automatically with team members who have project access. Release Notes2.0.0
1.0.0Initial release of the extension FAQQ: What if I don't have a code-mining server? A: You can still use the plugin to view vulnerability diagnostics and remediation guidance. AI explanations are optional and require a code-mining server. |