Owasp Zap Scanner
This project is a Azure DevOps task that allows users to integrate Owasp Zap security analysis into their VSTS pipelines.
Using the Owasp Zap Scanner
Follow the instructions below to add and configure the Owasp Zap Scanner in your build/release pipeline.
Prerequisites
If you want to scan a local server without internet access, you must have OWASP Zed Attach Proxy installed. For example, on a virtual machine or on a local installation that has access to the web application to be scanned.
If you want to scan an application that is exposed to the internet or has access to it through a virtual network accessed from Azure Pipelines, you can use the ZAP run option in Docker.
Both examples can be run with this extension: Owasp Zap Start Stop
The following article explains how to configure OWASP Zap and provides a detailed guide on how to do it.
Obtain the API Key required to access the ZAP API by following the instructions on the Official Documentation.
Add the Owasp Zap Scanner
Install the Owasp Zap Scanner in your Visual Studio Team Services account and search for the task in the available tasks. The task will appear in the Test section of the task list. Add it to your build/release task.
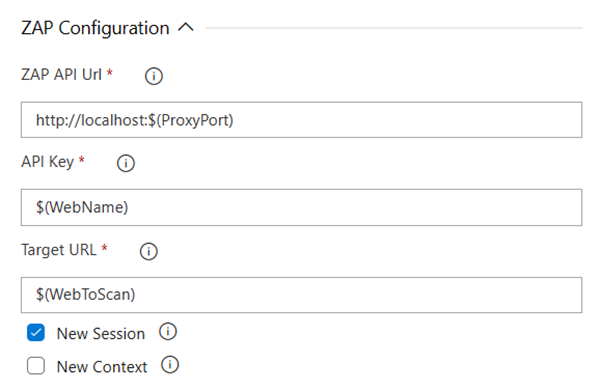
Required Options
- ZAP API Url : The fully qualified domain name (FQDN) with out the protocol. (Eg. zap.example.com)
- API Key : The API key for ZAP. Details about obtaining the API can be found on the Official Documentation
- Target URL : Target URL where the active scan is performed against.
Optional Options
- New Session : Creates a new session, optionally overwriting existing files. If a relative path is specified it will be resolved against the 'session' directory in ZAP 'home' dir.
- New Context : Create a new Context, optionally.
Ajax Spider Scan Options
This configuration section includes the parameters that need to be sent to perform the active scan against the target.
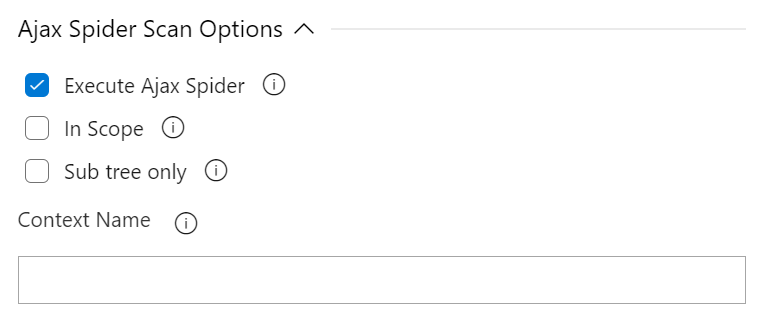
Available Options
- Execute Ajax Spider Scan : Enable to run a spider scan on the target.
- Subtree Only : (Optional) A boolean (true/false) indicating whether or not the crawl should be constrained to a specific path (default value is false). Enable to use the nodes underneath the one specified target to seed the Ajax spider.
- in Scope : (Optional) A boolean (true/false) indicating whether or not the scan should be restricted to 'inScope' only resources (default value is false). Enable to use the nodes underneath the one specified target to seed the Ajax spider.
- Context Name : (Optional) The name for any defined context. If the value does not match a defined context then an error will occur.
Spider Scan Options
This configuration section includes the parameters that need to be sent to perform the active scan against the target.
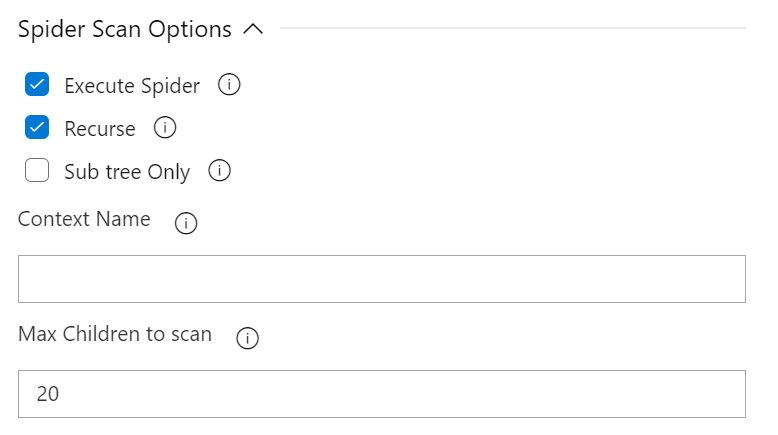
Available Options
- Execute Spider Scan : Enable to run a spider scan on the target.
- Recurse : (Optional) Enable to use the nodes underneath the one specified target to seed the spider.
- Subtree Only : (Optional) Enable to restrict the spider under the target url subtree.
- Context Name : (Optional) The name for any defined context. If the value does not match a defined context then an error will occur.
- Max Children : (Optional) Set to limit the number of children scanned.
Open Api Scan Options
This configuration section includes the parameters that need to be sent to perform the active scan against the target.
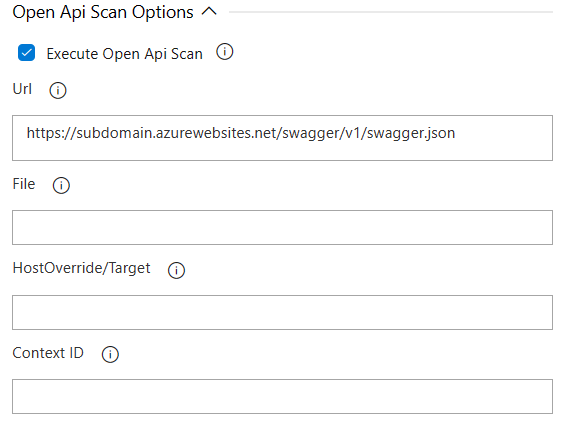
Available Options
Active Scan Options
This configuration section includes the parameters that need to be sent to perform the active scan against the target.
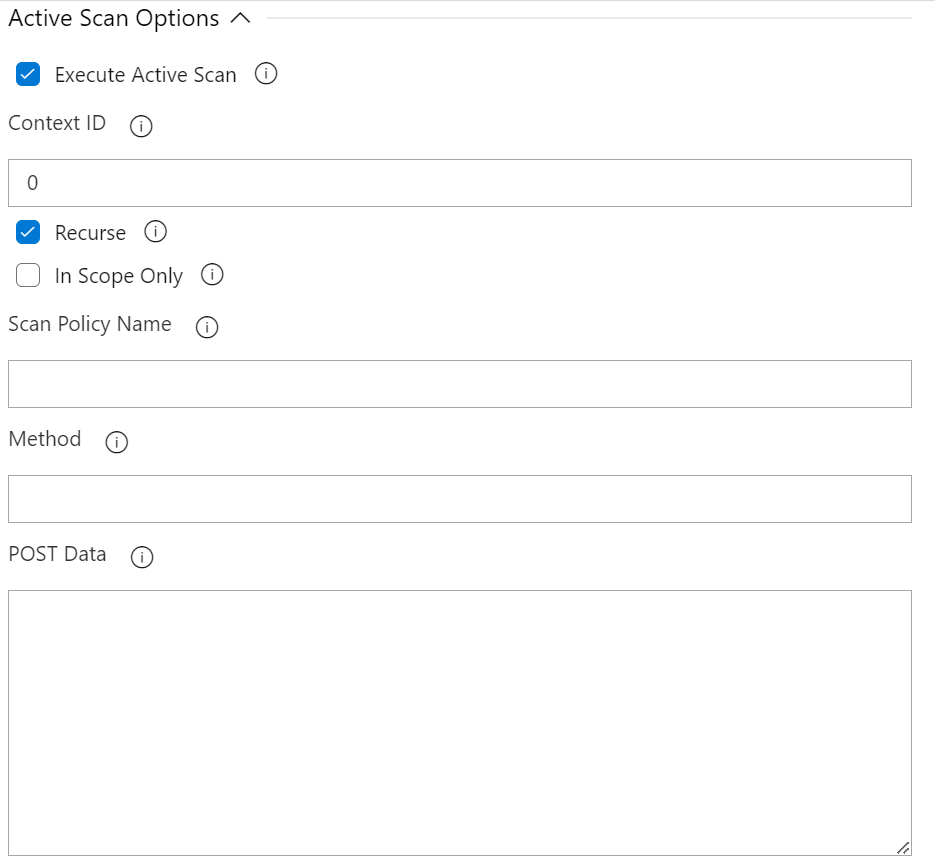
Available Options
- Execute Active Scan : Enable to run an active scan on the target.
- Context ID : (Optional) Context identifier of the Scan context.
- Recurse : (Optional) Set recurse option to scan URLs under the given target URL.
- In Scope Only : (Optional) Set In Scope only to true to constrain the scan to URLs that are in scope (ignored if a Context is specified).
- Scan Policy Name : (Optional) Scan Policy Name allows to specify the scan policy (if none is given it uses the default scan policy).
- Method : (Optional) Allow you to select a given request in conjunction with the given URL.
- POST Data : (Optional) Allow you to select a given request in conjunction with the given URL.
This configuration section includes the parameters that need to be sent to perform the active scan against the target.
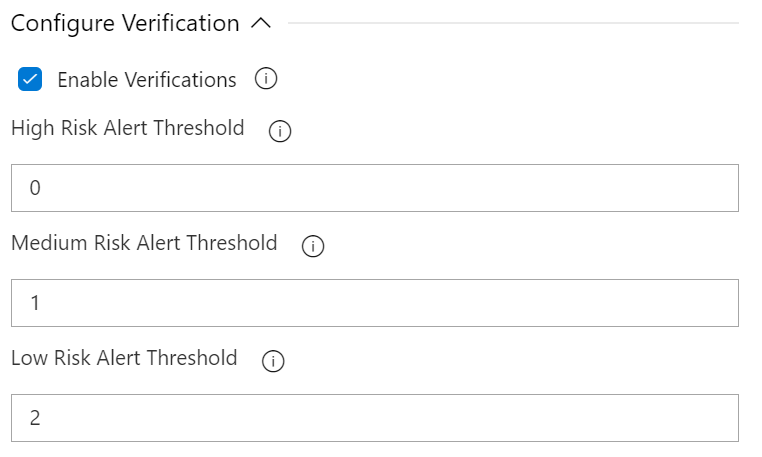
Available Options
- Enable Verifications: Enable to add thresholds for security risk types and fail the build if the threshold is exceeded.
- High Risk Alert Threshold: Maximum number of allowed High Risk Alerts. The build will fail if the number of high risk alerts equals or exceeds this threshold.
- Medium Risk Alert Threshold: Maximum number of allowed Medium Risk Alerts. The build will fail if the number of medium risk alerts equals or exceeds this threshold.
- Low Risk Alert Threshold: Maximum number of allowed Low Risk Alerts. The build will fail if the number of low risk alerts equals or exceeds this threshold.
This configuration section includes the parameters that need to be sent to perform the active scan against the target.
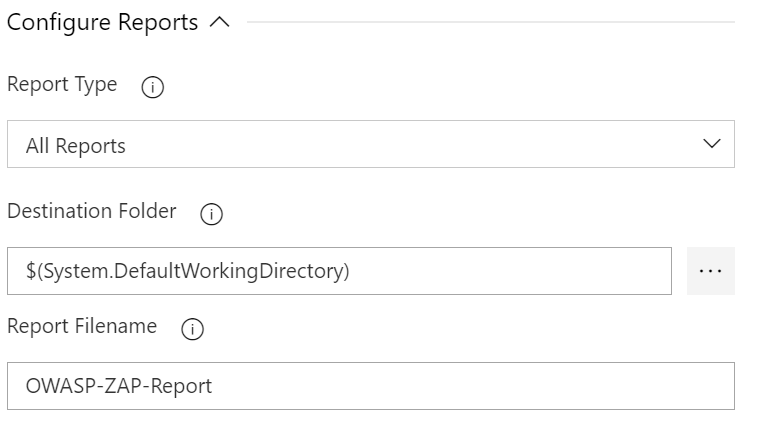
Available Options
- Report Type : Select the type of report you want generated. Available types are HTML, XML, Markdown or All.
- Destination Folder : The destination folder that the report file is created. You can use variables. Eg. $(agent.builddirectory).
- Report Filename : Name of the report file, without the extension. Extension is determined by the Report Type. Eg. OWASP-ZAP-Report-2017-00-00.
Additional
To complement the use of this extension it is recommended to use:
https://marketplace.visualstudio.com/items?itemName=solucionespsg.OwaspZapOnPremiseStartStop
With the extension OwaspZapStartStop VSTS task start, stop, download template and transform test result on Windows Server OnPremise (selft hosted) and run in Docker on Linux (Agent pool Azure Pipelines).
Full example
Agent Job:
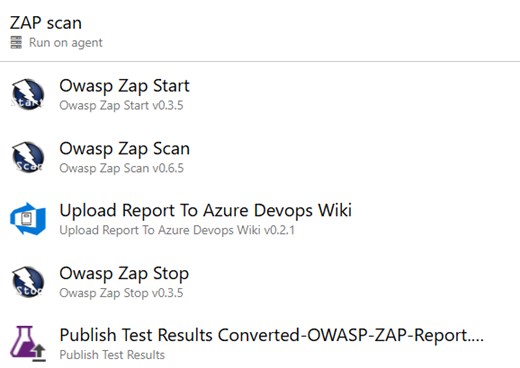
Owasp Zap Start
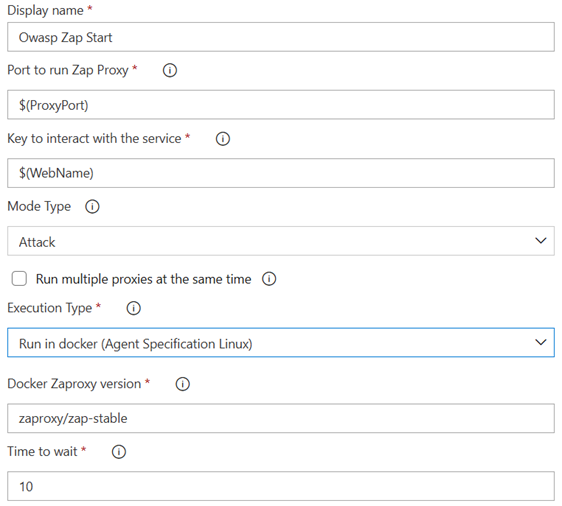
If you want to run it OnPremise select: "Onpremise/Virtual (Self-hosted Agent Specification Windows)"
If you want to run it on Azure Pipelines Hosted (linux option) select: "Run in docker (Agent Specification Linux)"
Owasp Zap Scan
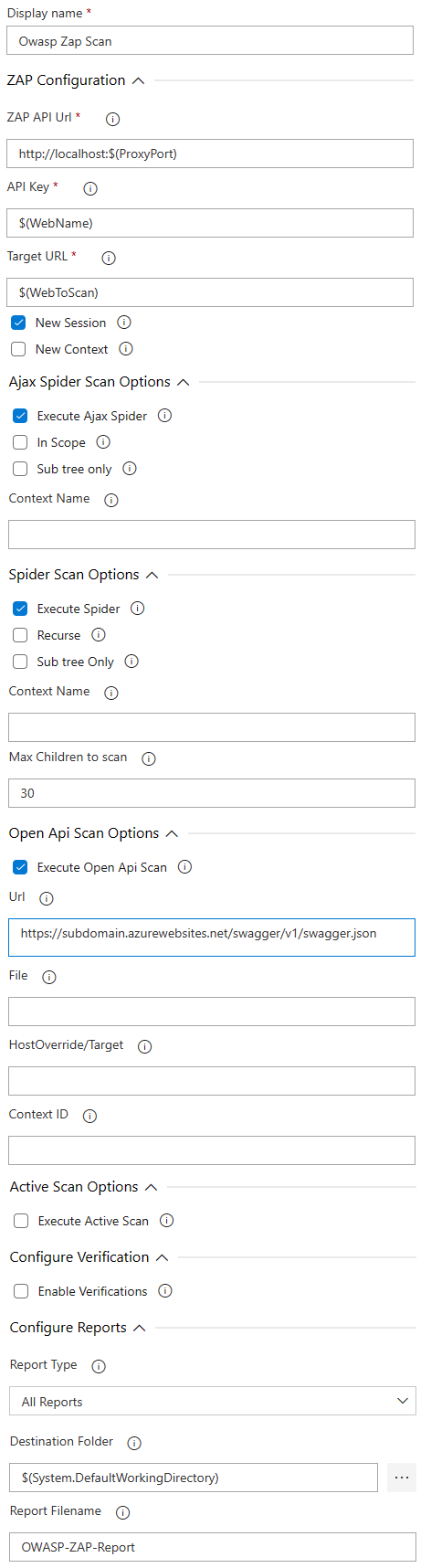
"Owasp Zap Scan" can be downloaded from here: https://marketplace.visualstudio.com/items?itemName=solucionespsg.owasp-zap-scan-psg
Upload Report To Azure Devops Wiki
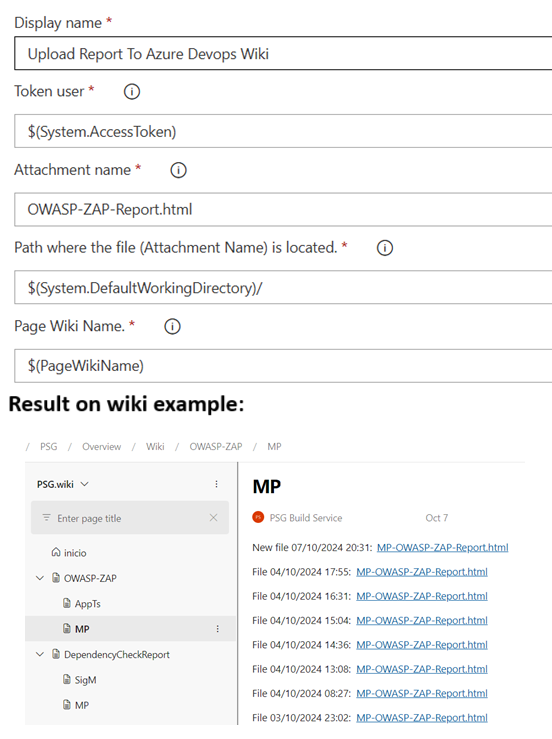
"Upload Report To Azure Devops Wiki" can be downloaded from here: https://marketplace.visualstudio.com/items?itemName=solucionespsg.UploadReportToAzureDevopsWiki
Owasp Zap Stop
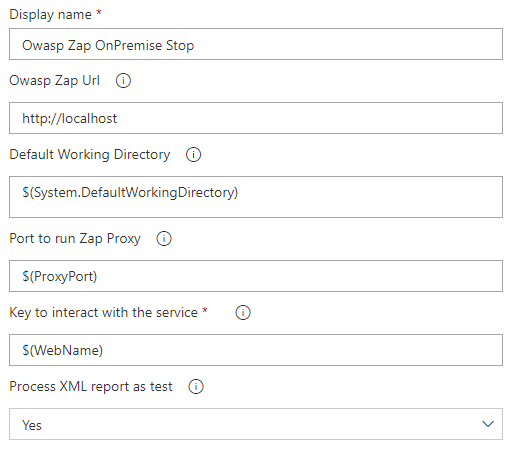
Publish Test Result Converted
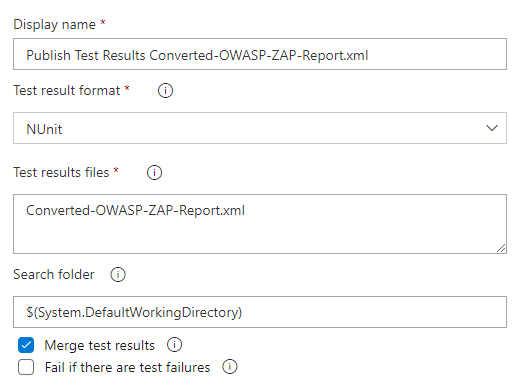
Then there is this "Publish Test Result" this is from Microsoft: https://learn.microsoft.com/en-us/azure/devops/pipelines/tasks/reference/publish-test-results-v2
Example of variables

After finishing the tasks we access the tests:
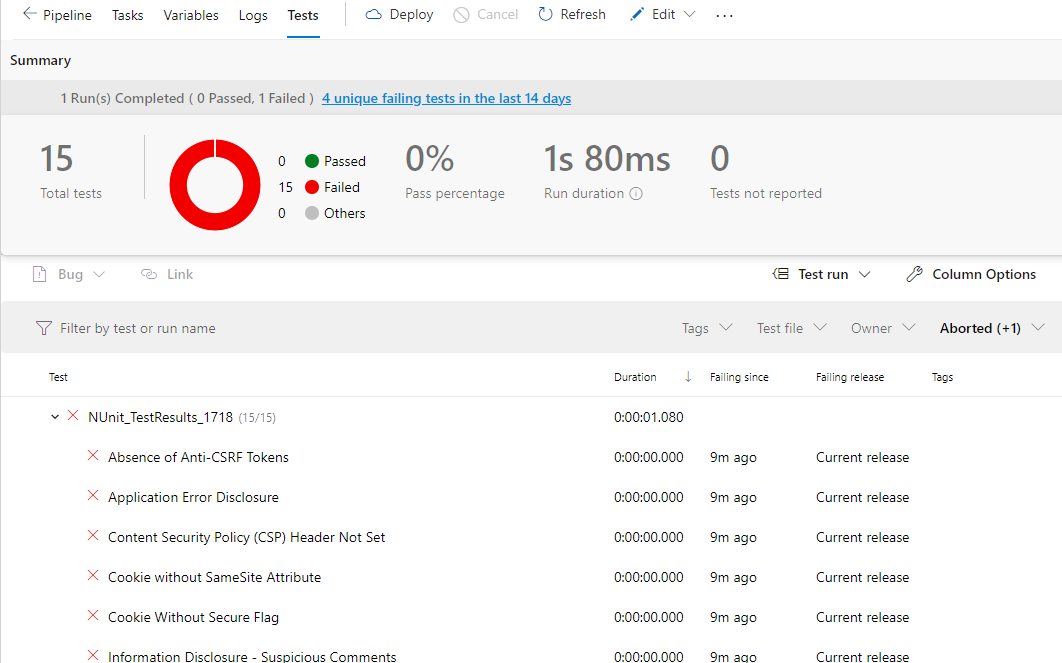
Help to continue development.
If it helped you. You can help me:
https:// paypal.me/solucionespsg












