OWASP Dependency Check
Dependency-Check is a software composition analysis utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities. Currently, Java and .NET are supported; additional experimental support has been added for Ruby, Node.js, Python, and limited support for C/C++ build systems (autoconf and cmake). The tool can be part of a solution to the OWASP Top 10 2017 A9-Using Components with Known Vulnerabilities previously known as OWASP Top 10 2013 A9-Using Components with Known Vulnerabilities.
The OWASP Dependency Check Azure DevOps Extension enables the following features in an Azure Build Pipeline:
Software composition analysis runs against package references during build on both Windows and Linux build agents.
Export vulnerability data to HTML, JSON, XML, CSV, JUnit formatted reports
Download vulnerability reports from the build's artifacts
GitHub Repository
The extension maintainers do not monitor the Marketplace Question & Answers. Please use the Azure DevOps Dependency Check repository for questions, issues, or enhancements.
Installation and Configuration
Install the OWASP Dependency Check extension into your Azure DevOps Organization.
Open an Azure DevOps project and browse to the Pipelines / Builds.
Press the Edit button to modify the pipeline definition.
Press the + icon to add a new OWASP Dependency Check build task.
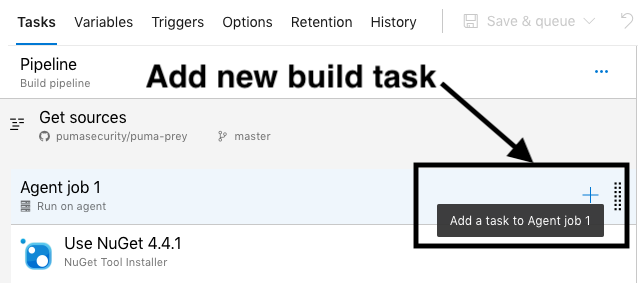
Search for the OWASP Dependency Check task and press the Add button.
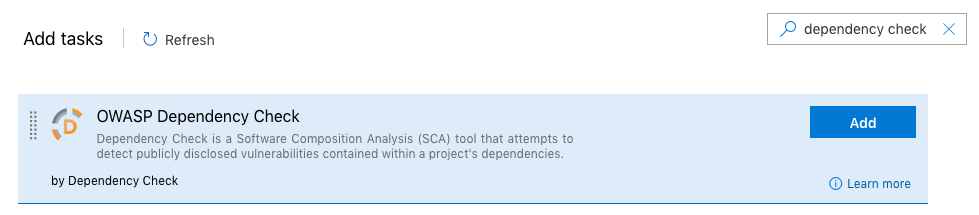
Configure the build task with the appropriate Dependency Check Command Line Arguments.
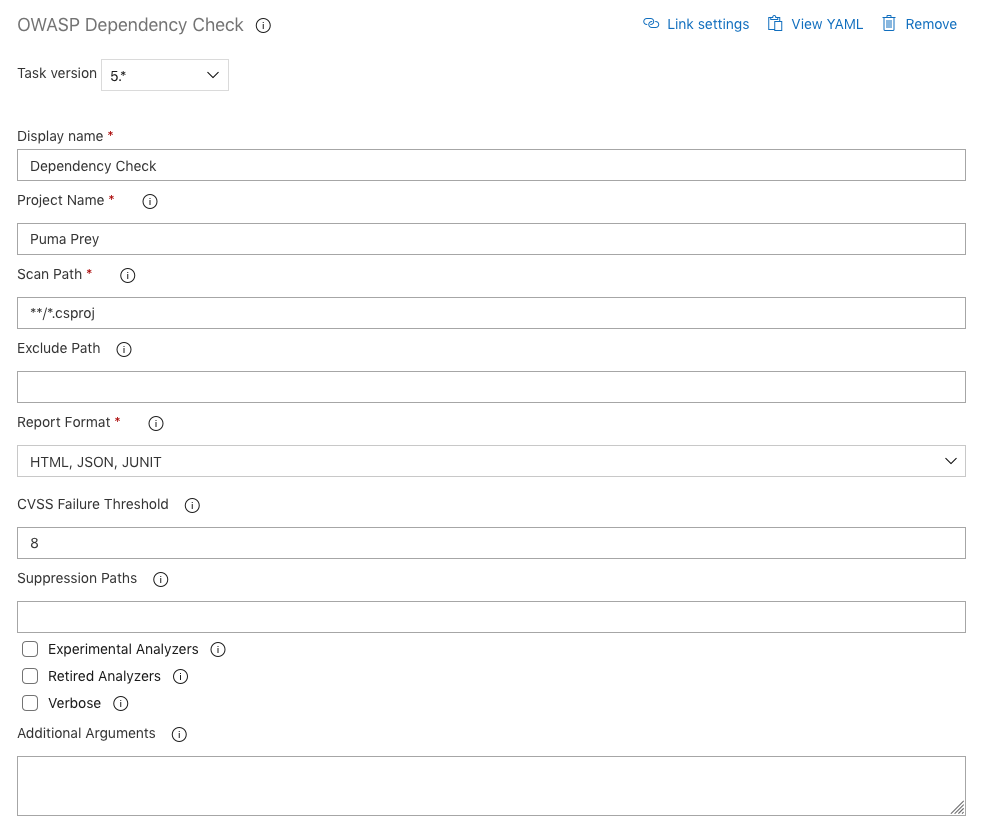
Executing Dependency Check
Execute the pipeline and wait for the build to complete.
Review the build logs and ensure the the Dependency Check task successfully completed.
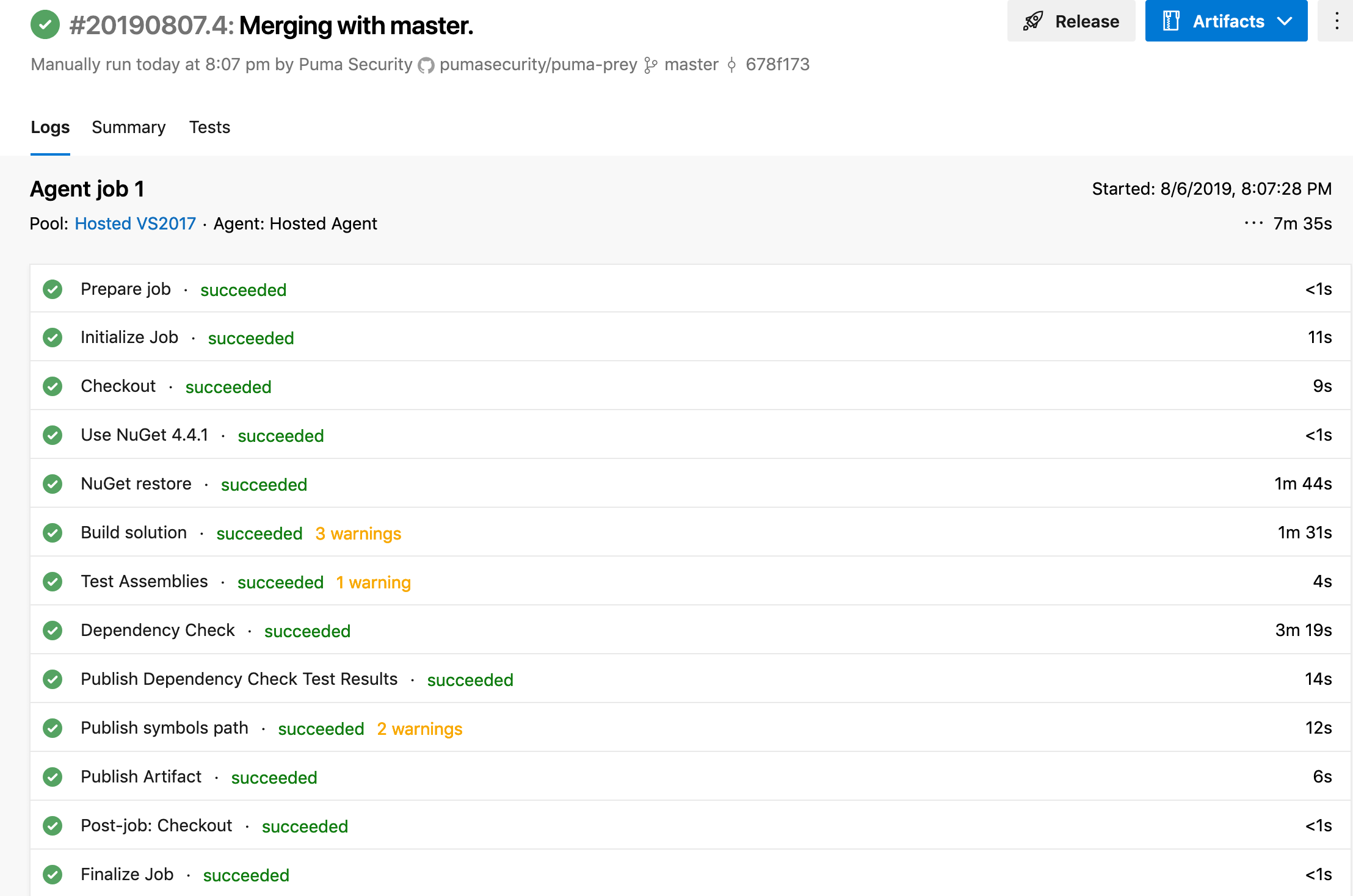
Click on the Dependency Check build task to view the build output.
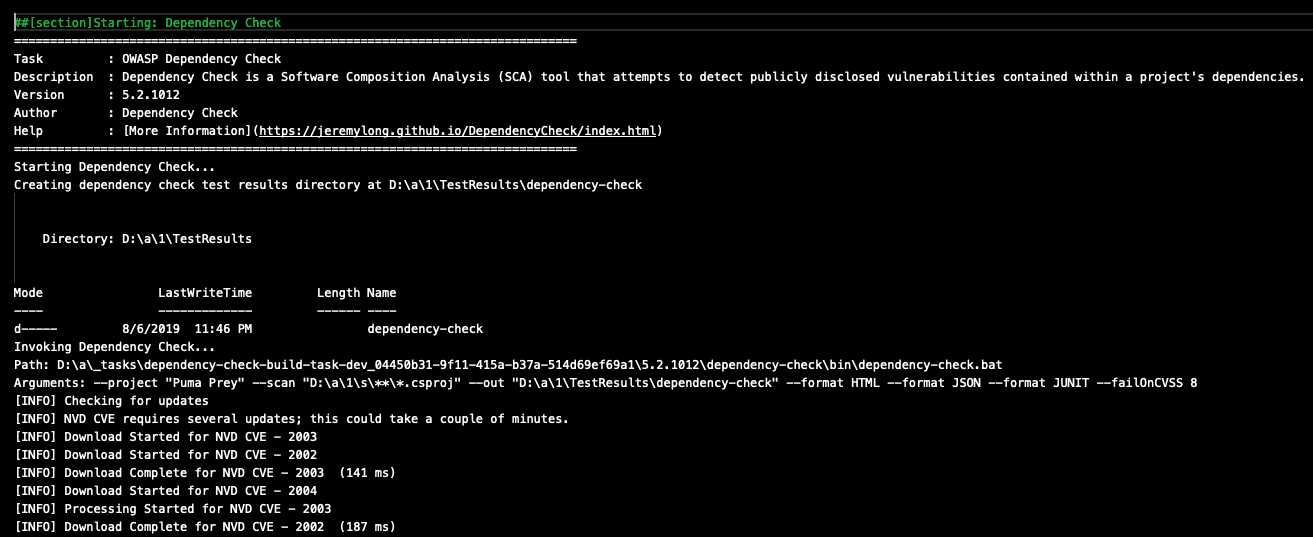
Dependency Check Reports
Each of the selected report formats are uploaded to the Artifacts for downloading.
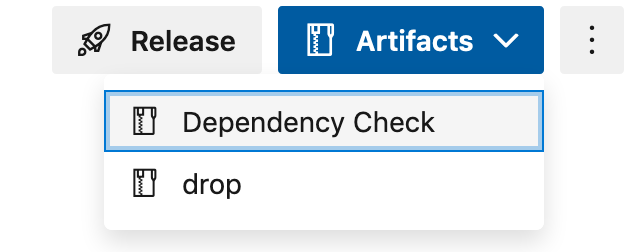
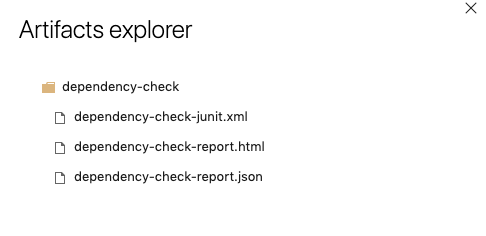
Select Dependency Check to open the Artifact Explorer and download the Dependency Check reports.
Dependency Check supports exporting the results to JUNIT formatted test results. To parse the JUNIT test results, create a new Publish Test Results build task with the following configuration.
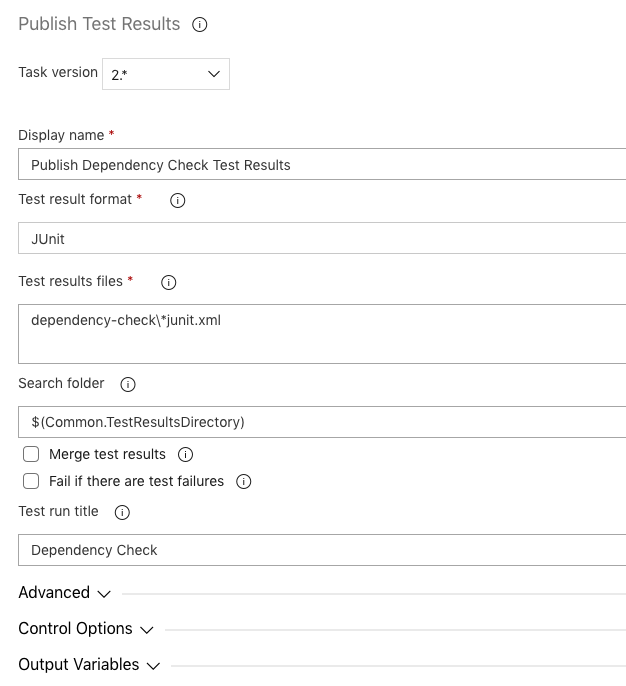
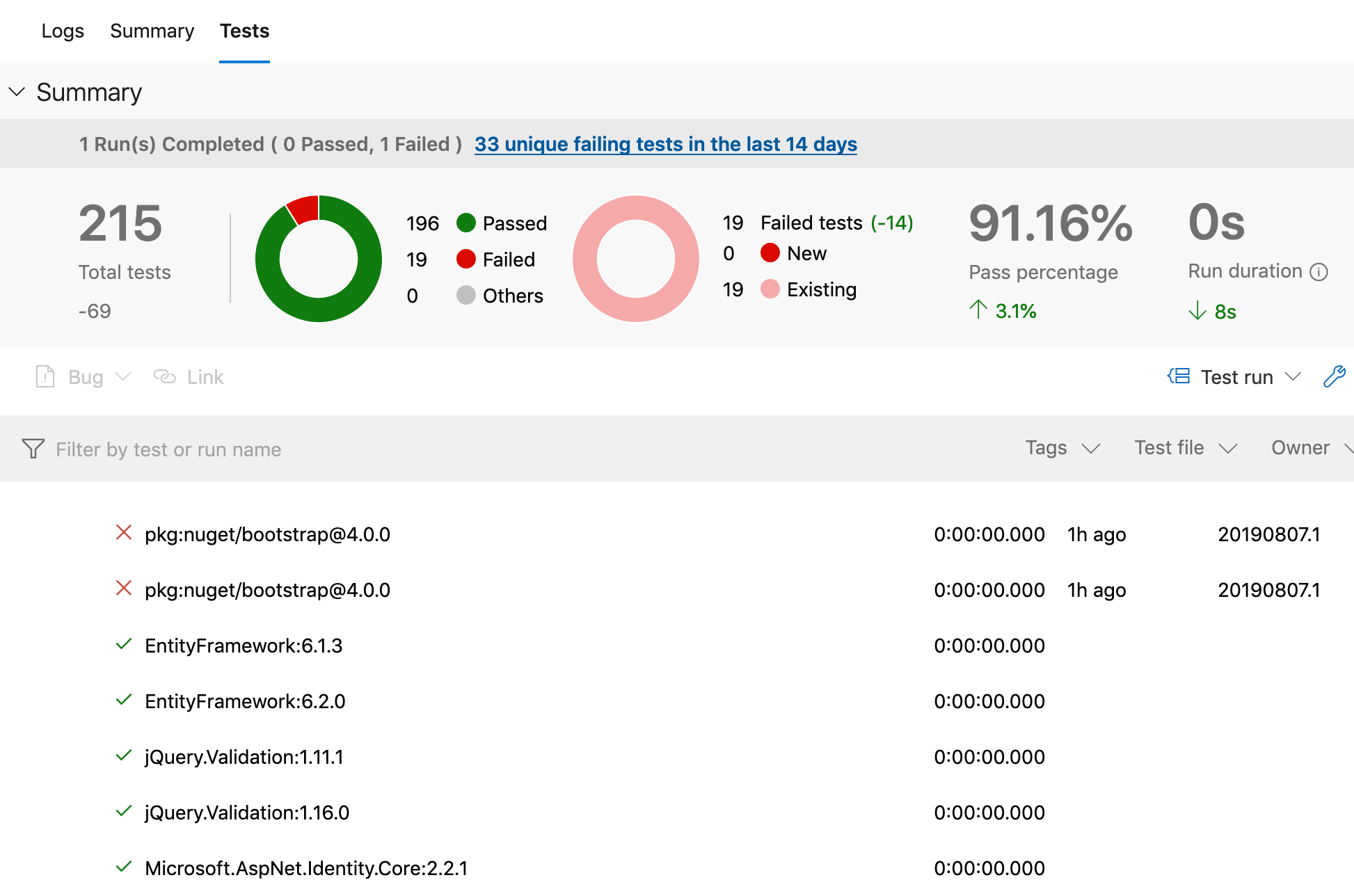
View the Tests screen to view the passing and failing Dependency Check tests.
Learn More
More details on configuring and running Dependency Check can be found at https://dependency-check.github.io/DependencyCheck/.
Supported Environments
- The Dependency Check Azure DevOps extension has been converted to TypeScript as of version 6.0. With this update, both Linux and Windows build agents are supported.
Contributors
First thank Jeremy Long and the folks working on the OWASP Dependency Check project.
The following contributor(s) help maintain the Azure DevOps extension:











