
See where your AI code takes root — and how it grows over time
CodeRoot.ai turns everyday editing into a simple, trustworthy picture of creation: Human vs Automation, with out-of-band and preexisting contributions called out explicitly. With a shared view of what’s happening in your codebase, teams can talk about impact and outcomes with facts, not anecdotes.
Who it’s for (at a glance)
- Developers: a fair view of your work and easy validation of recent changes
- Tech leads: clarity on AI usage and ownership; hotspots without guesswork
- Managers: objective trends you can compare over time and across teams
- Executives: visibility into AI’s contribution to production, not just change volume
What you’ll see
CodeRoot.ai provides a shared lens on creation using the PCM 1.1.8 category set:
- Automation — AI-assisted and trusted automation (includes “observed” tool output)
- Human — deliberate human edits
- Preexisting — baseline content brought in with the workspace
- Out-of-band — external edits or unknown attribution that needs review
All analysis runs locally. Reports are deterministic: the same inputs produce the same outputs, so comparisons remain stable over time.
Install from the VS Code Marketplace
- In VS Code, open the Extensions view
- Search for “CodeRoot.ai” by SettleTop and click Install
- Reload if prompted
Quick start (2 minutes)
- Open a folder that’s a Git repository
- Run “CodeRoot: Initialize CodeRoot”
- Run “CodeRoot: Generate Report” and open it
That’s it. A small .coderoot/ folder appears in your repo (hidden by default). You can toggle its visibility any time from the Quick Menu.
Open “CodeRoot: Settings / Quick Menu.” From one place you can:
- Show/hide the
.coderoot folder in Explorer
- Switch report scope: Modified vs All files
- Run an Identity Sweep to unify aliases
- Open the
.coderoot folder
- (Optional) Enable CI script maintenance
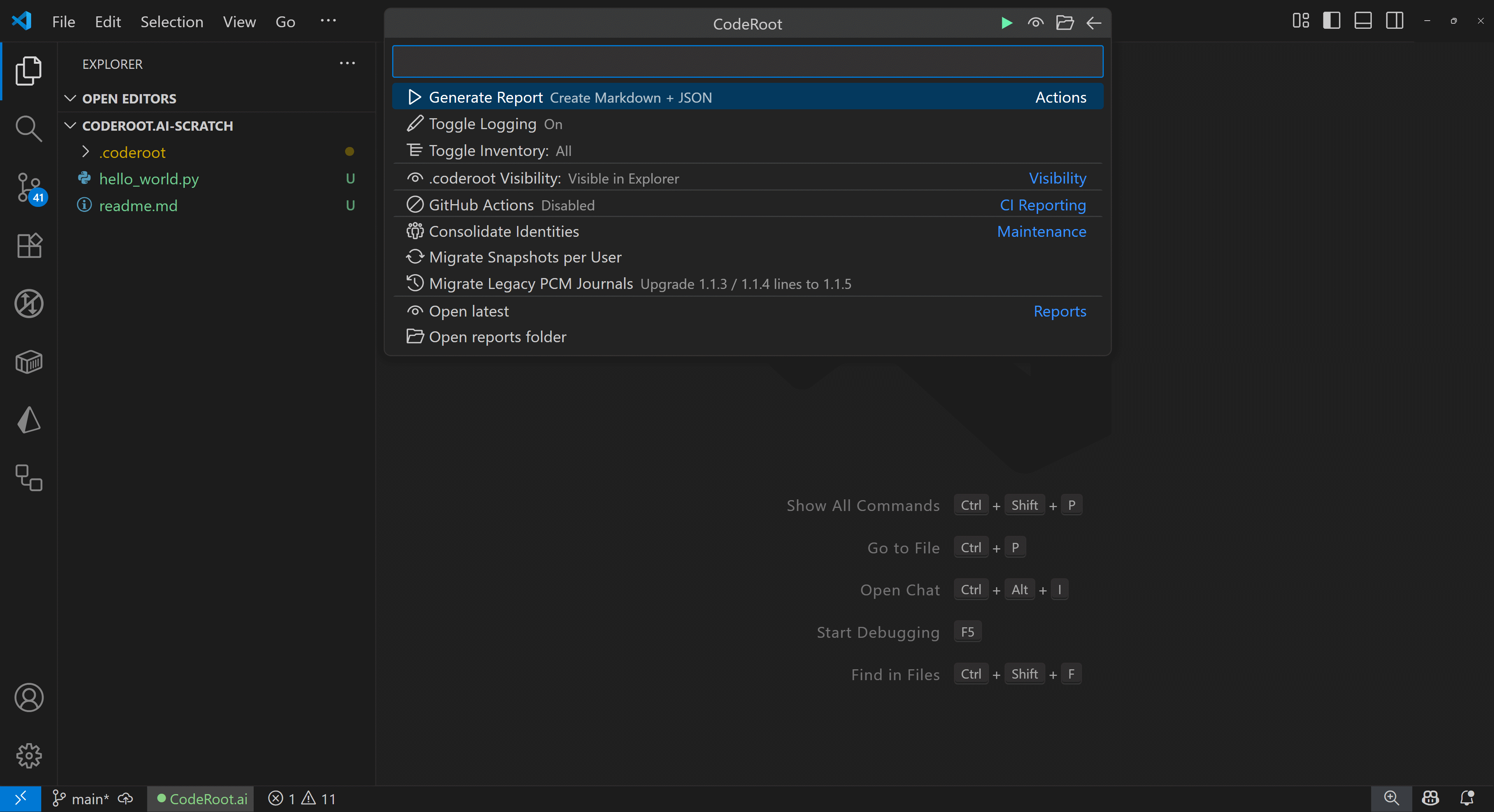
Quick Menu — visibility, scope, identity, and CI
Privacy and safety (designed-in)
- Local‑first: analysis runs on your machine; no servers are contacted
- Text‑free journals: we store counts, byte ranges, and hashes — not your code
- Deterministic outputs: identical inputs produce identical reports for trustworthy comparisons
Note for implementers: CodeRoot still emits PCM 1.1.7 records on disk while adopting the stricter 1.1.8 origin/category semantics above. Readers accept legacy 1.1.3–1.1.7.
Common actions
- Toggle .coderoot visibility: “CodeRoot: Toggle .coderoot Visibility”
- Switch scope: “CodeRoot: Inventory Mode — Modified/All”
- Run Identity Sweep: “CodeRoot: Run Identity Sweep” (unifies aliases for clean per‑person totals)
- Consolidate identities now: “CodeRoot: Consolidate Identities Now”
- Open .coderoot folder: “CodeRoot: Open .coderoot Folder”
Advanced (optional)
- CI reports: enable “CI Scripts Maintenance” in the Quick Menu to seed
.github/scripts/ and a workflow; add .github/.coderoot-ci.lock to opt out
- Migrate legacy journals: “CodeRoot: Migrate Legacy PCM Journals” to upgrade older entries in place
Requirements
- VS Code 1.90.0 or later
- A Git repository workspace (recommended)
- A GitHub hosted project for CI integration (optional)
Troubleshooting
- “I don’t see
.coderoot/.” Run “CodeRoot: Initialize CodeRoot” in the workspace root
- “Git isn’t available.” Enable the VS Code Git extension
- “Report looks sparse.” Make sure you’ve worked in this repo after initializing; the report summarizes what happened locally
License and support
CodeRoot.ai is distributed under the following LICENSE.md. For questions or feedback, contact support@coderoot.ai.
© 2025 SettleTop, Inc.




 Quick Menu — visibility, scope, identity, and CI
Quick Menu — visibility, scope, identity, and CI


