Aikido Security Extension for Visual Studio Code
Secure code as it’s written (and generated). Real-time static analysis (SAST), secrets, and open-source dependency (SCA) scanning, plus AI AutoFix for one-click fixes so you can address issues before they reach PRs.
Requirements
What it does
- Real-time scanning on open/save for code security problems, secrets, and open source dependency vulnerabilities. Findings appear inline, in sidebar and with hover details for fast triage.
- AI integration with MCP seamlessly sets up the Aikido MCP server to scan newly generated or modified code for vulnerabilities, allowing the agent to detect and fix issues directly in its workflow.
- AI AutoTriage noise reduction: Aikido prioritizes and de-emphasizes issues based on reachability/ and impact.
- AI AutoFix in the IDE: When a fix is available, preview and apply a safe change for supported SAST and SCA findings, without leaving VS Code.
- Policy-aware and custom SAST results in the IDE ensure workspace severities, ignores, and Aikido-defined custom SAST rules are applied so developers see the most relevant issues first.
Usage
Install & authenticate
- Install the Aikido extension.
- Connect to Aikido or enter your PAT
- If needed, create a token manually in Aikido and paste it when prompted.
- You’re ready to scan! Issues will be highlighted as you edit.
Scanning
The integration scans your codebase for secrets, API keys, SAST code issues and open-source dependency vulnerabilities. It runs scans whenever you open or save a file.
Every time you make and save changes in a file, a scan runs. If any issues are detected, they are highlighted in the editor and Aikido sidebar. When you hover over a detected SAST issue, additional context about the problem is provided.
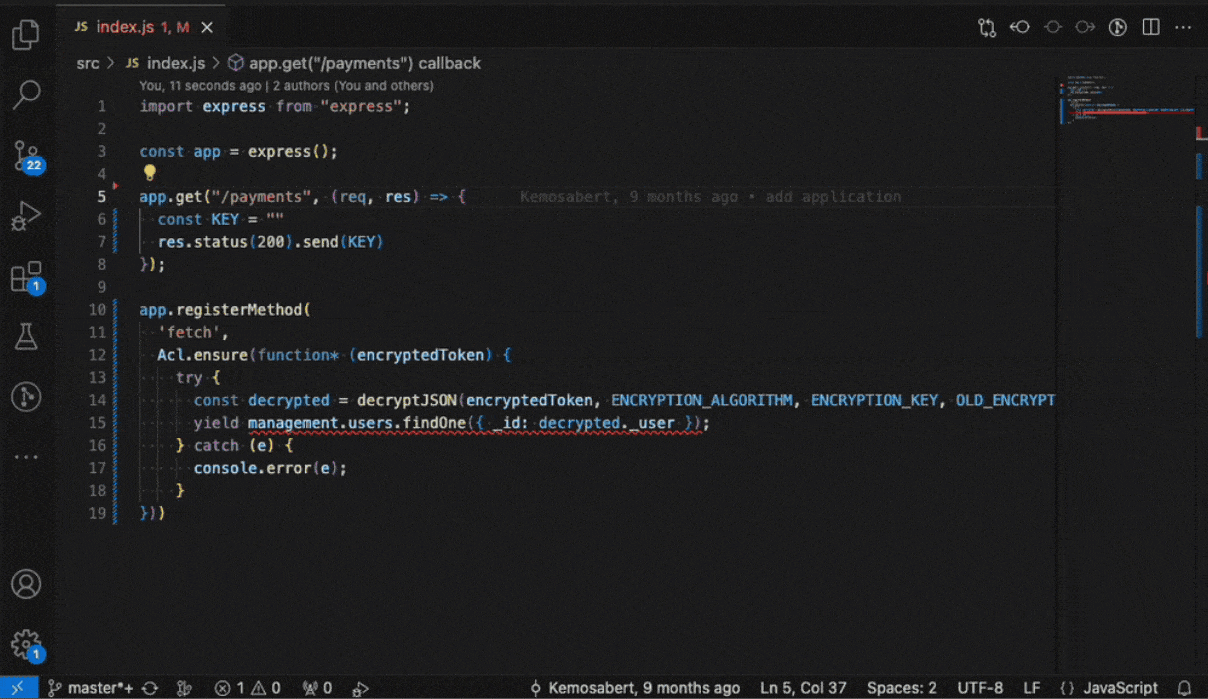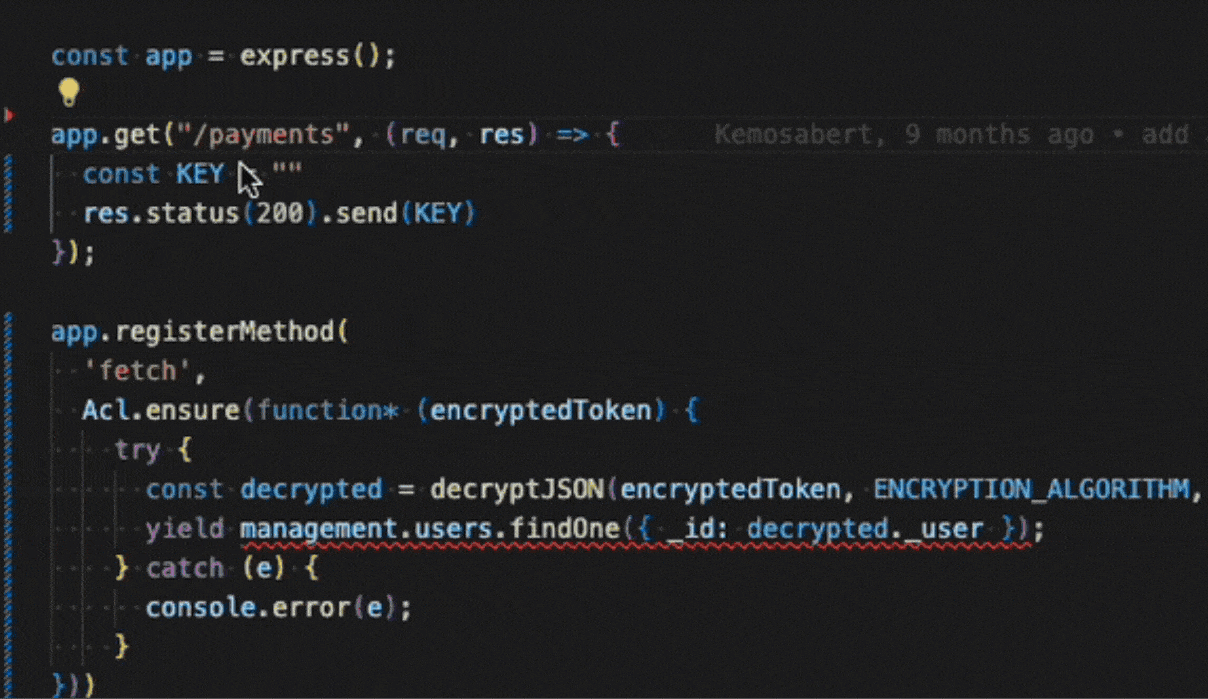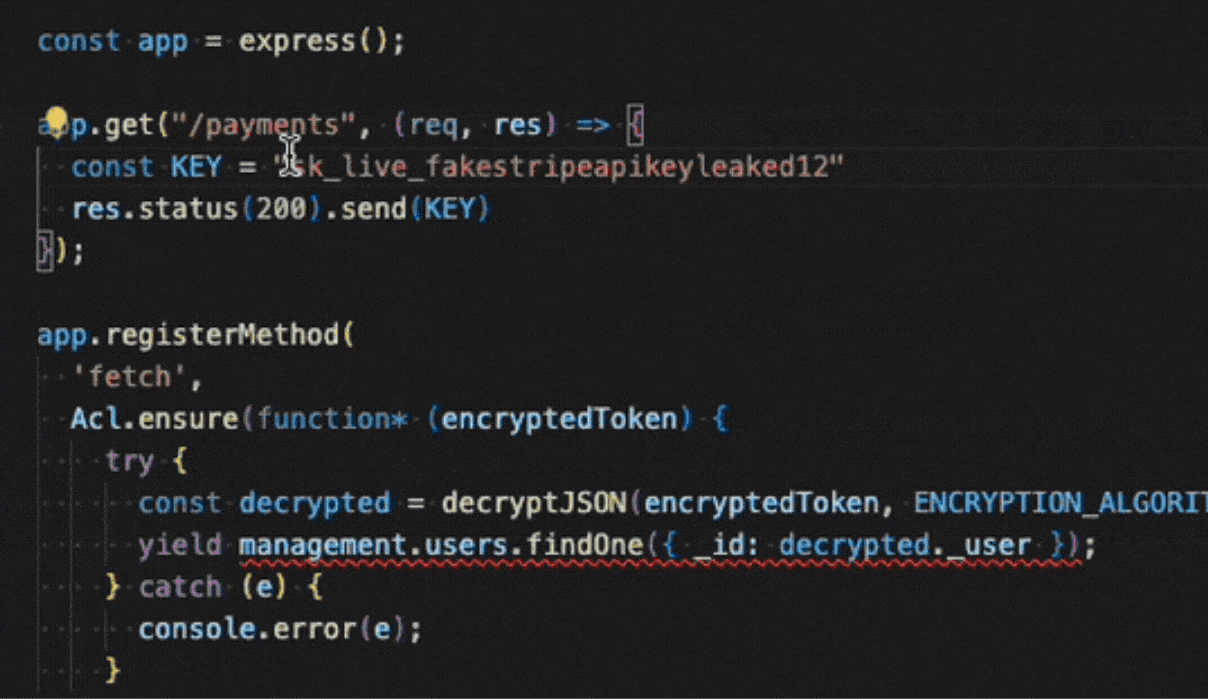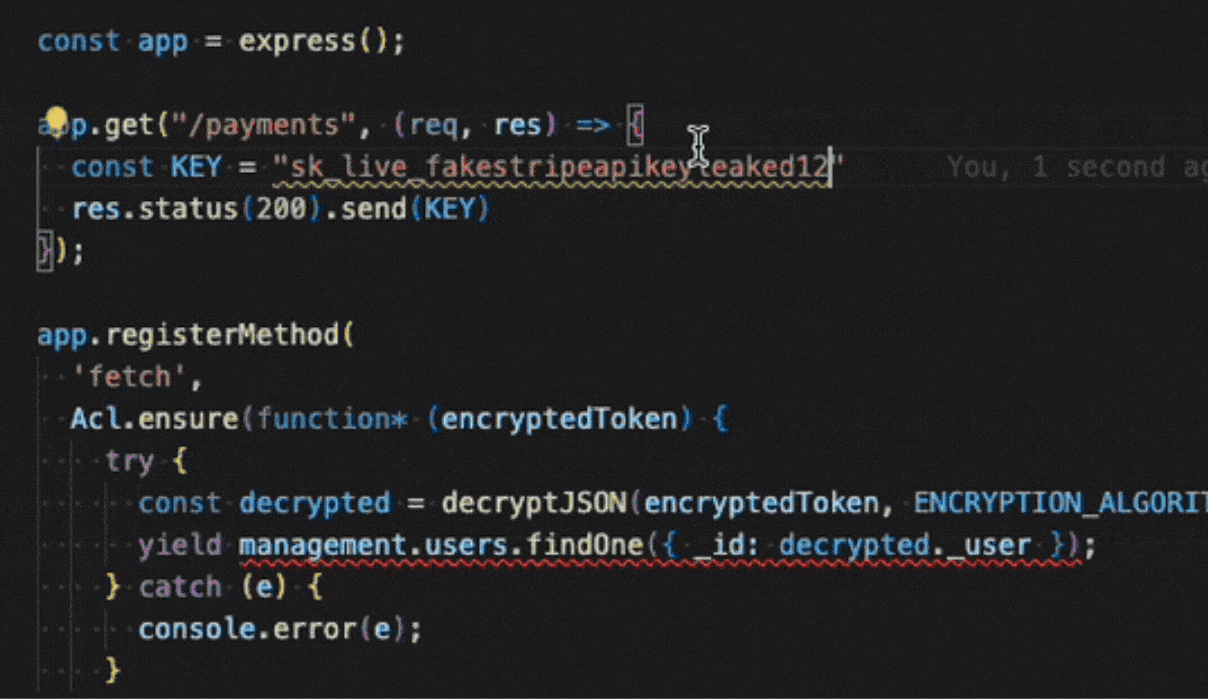
Aikido AI AutoFix and AutoTriage
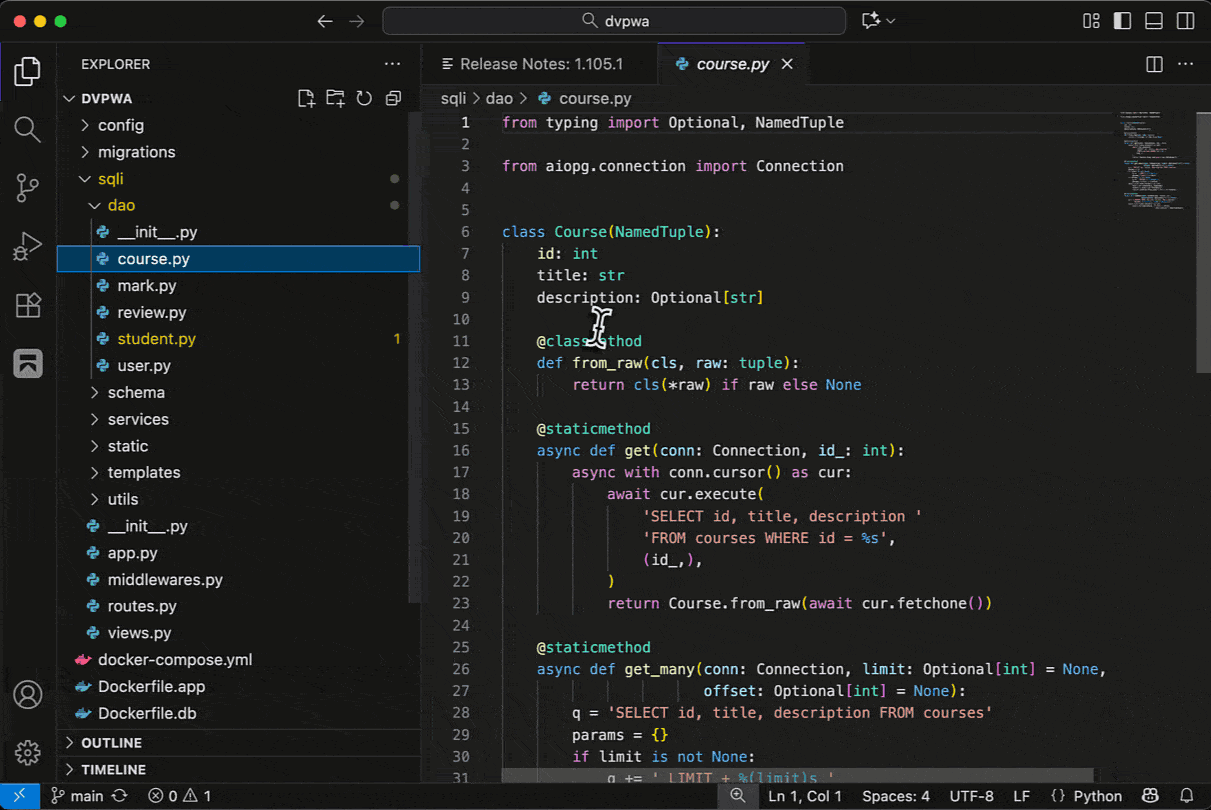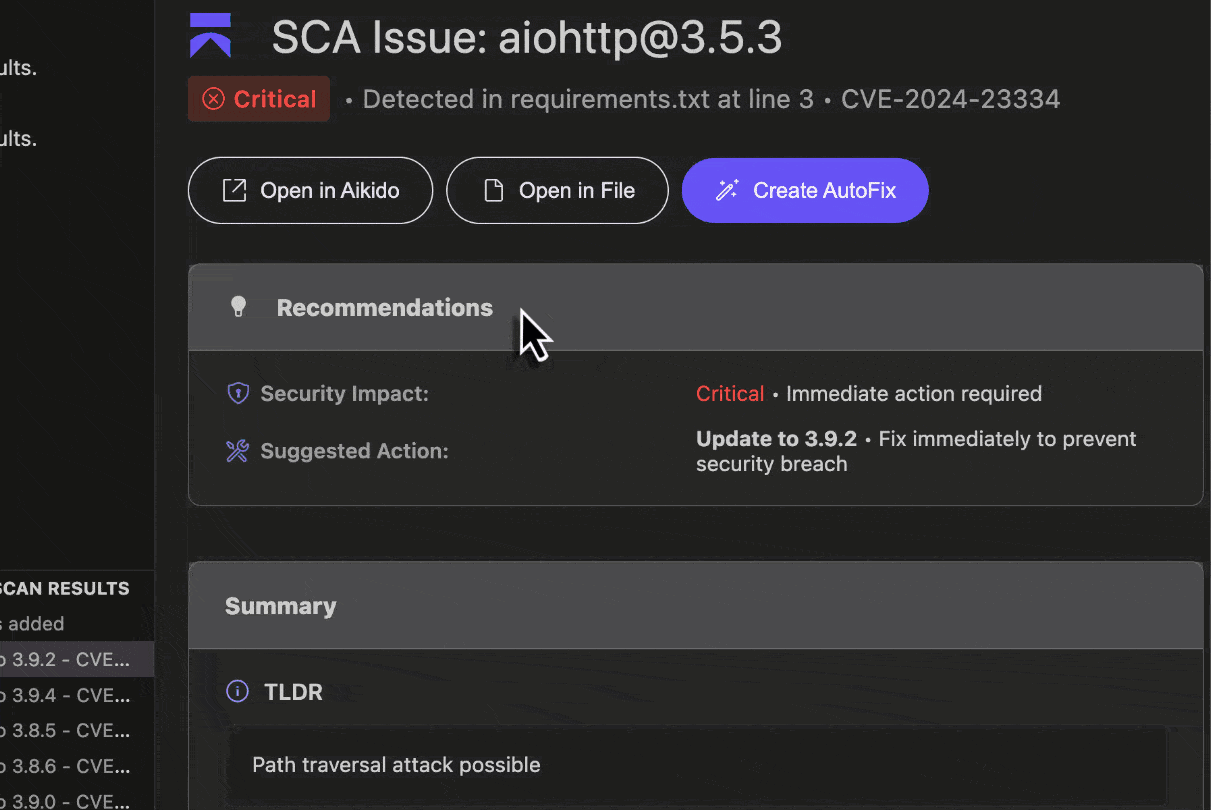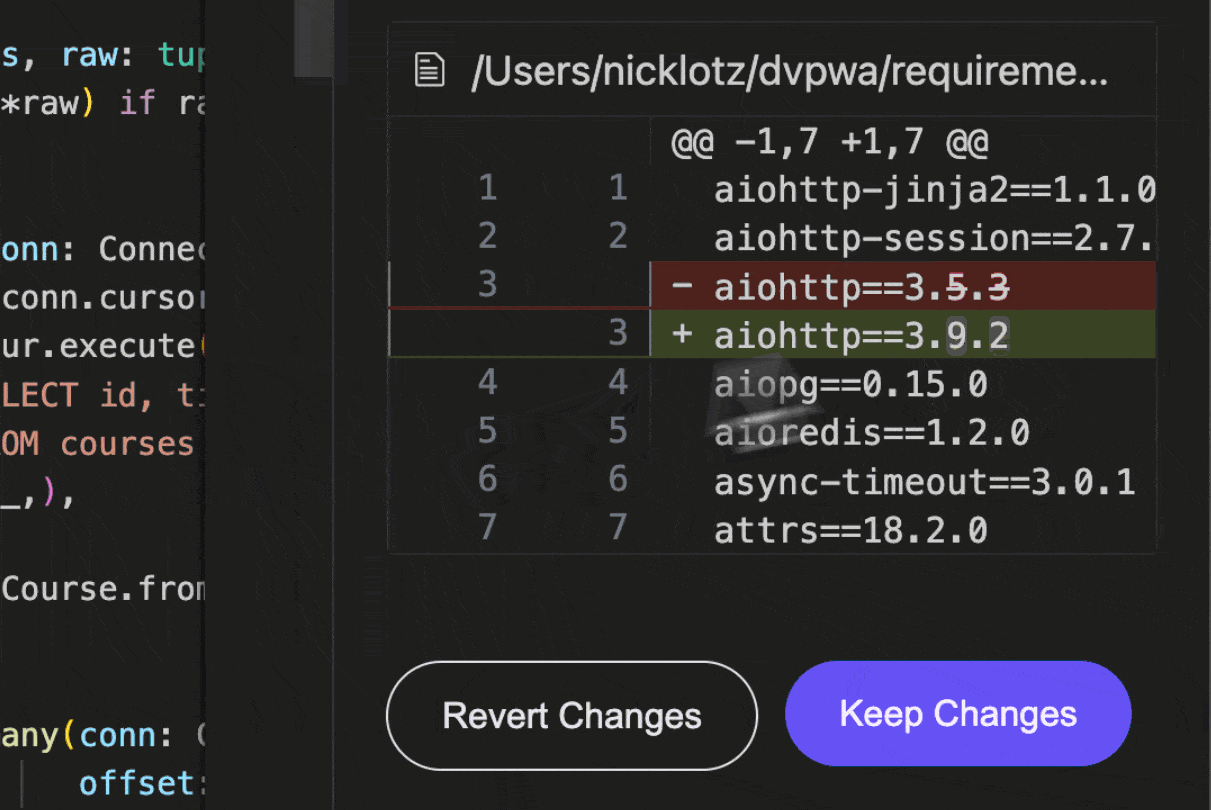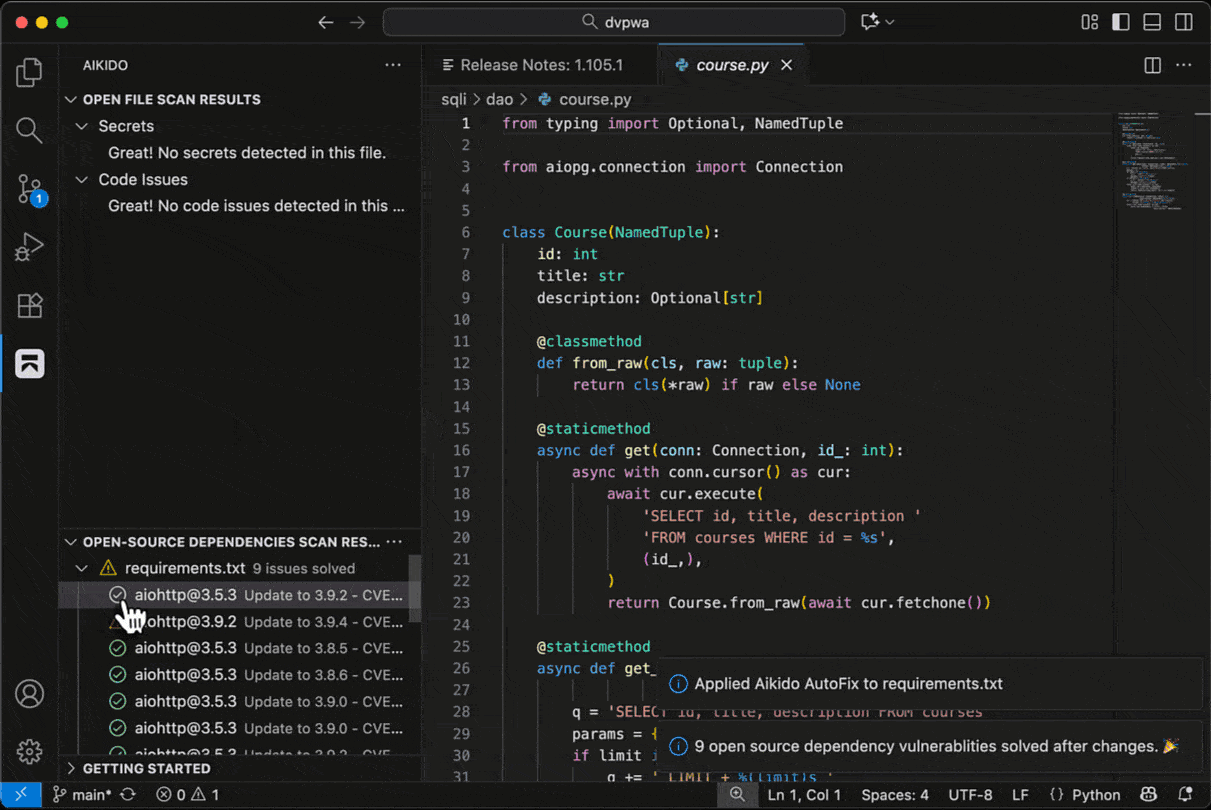
For supported SAST and SCA issues, Aikido will provide the option to assess the issue’s impact with AI AutoTriage, and optionally apply a code fix with AI AutoFix. This fix is applied directly in IDE.
SAST AutoFix
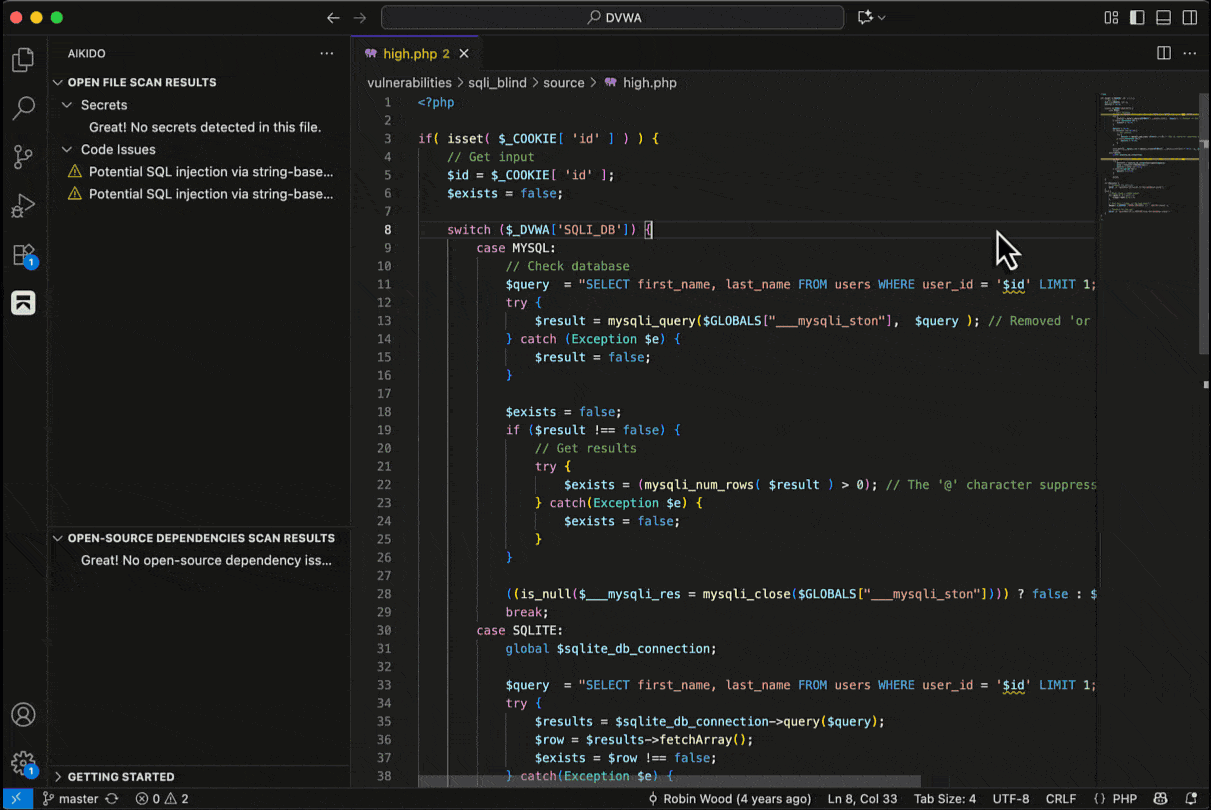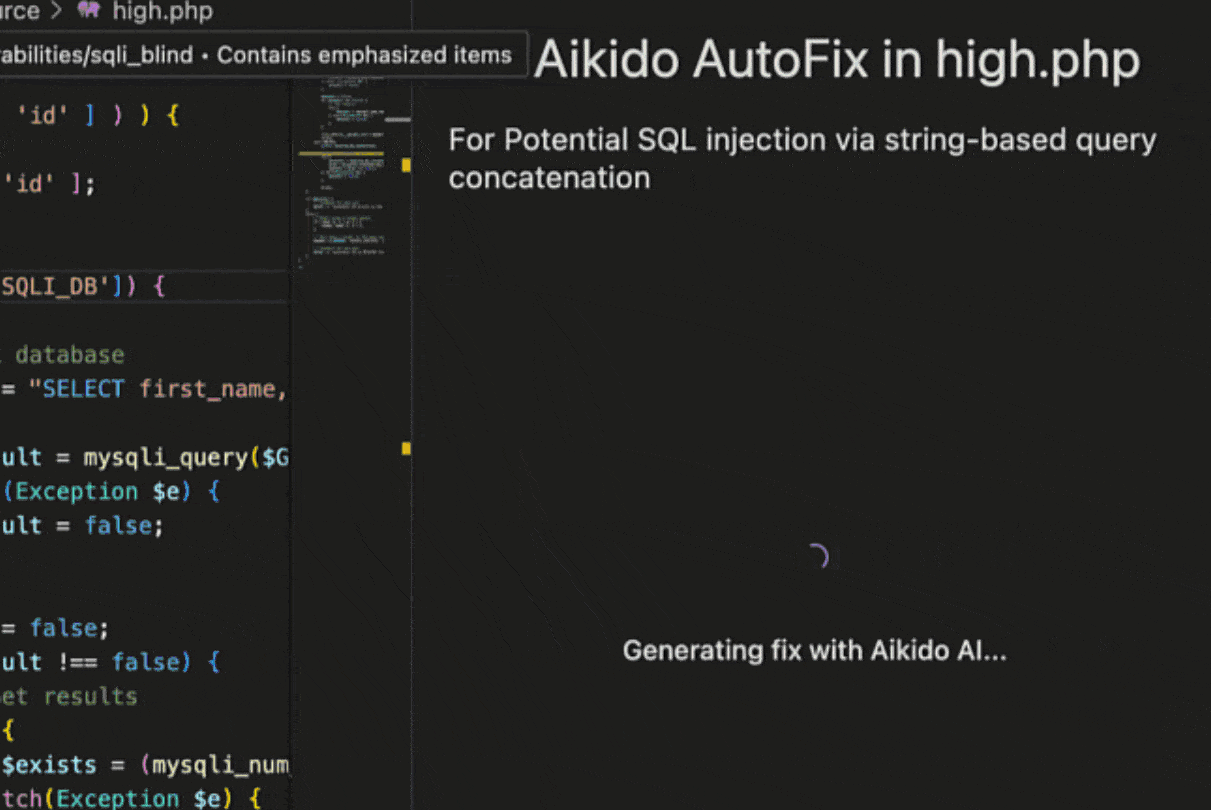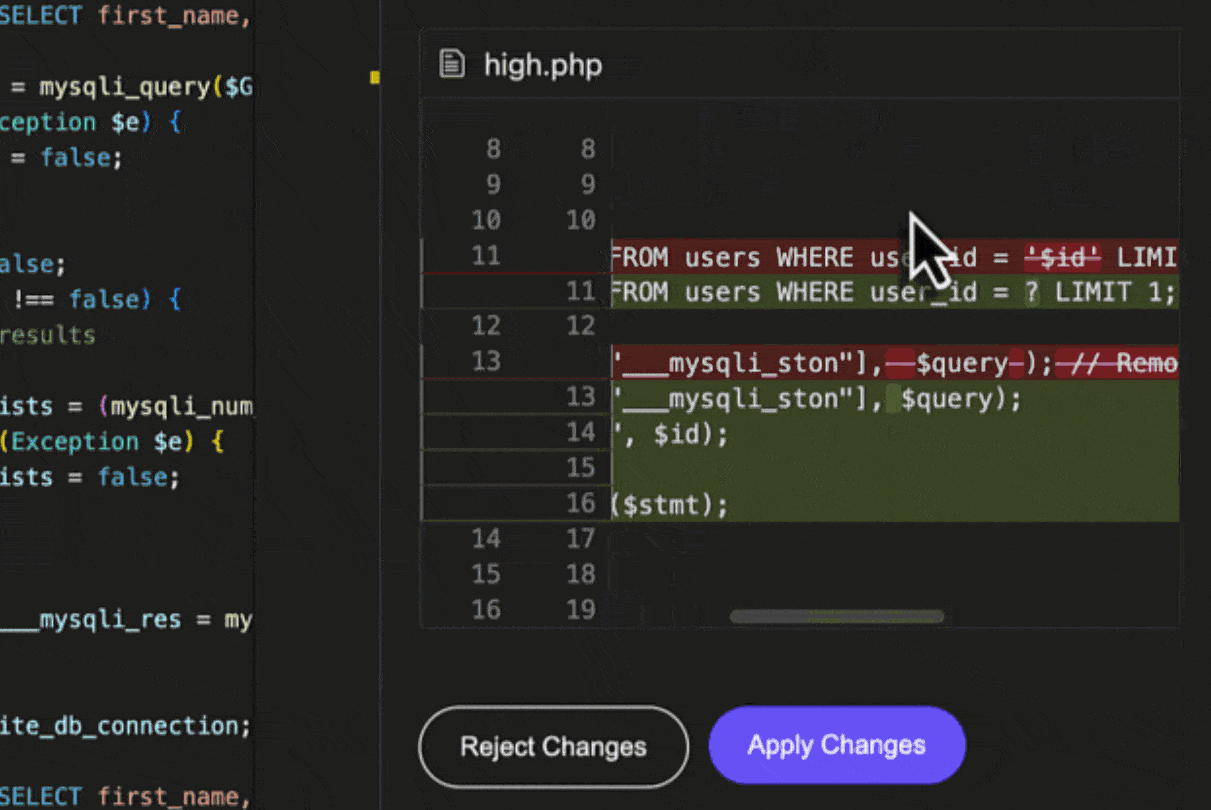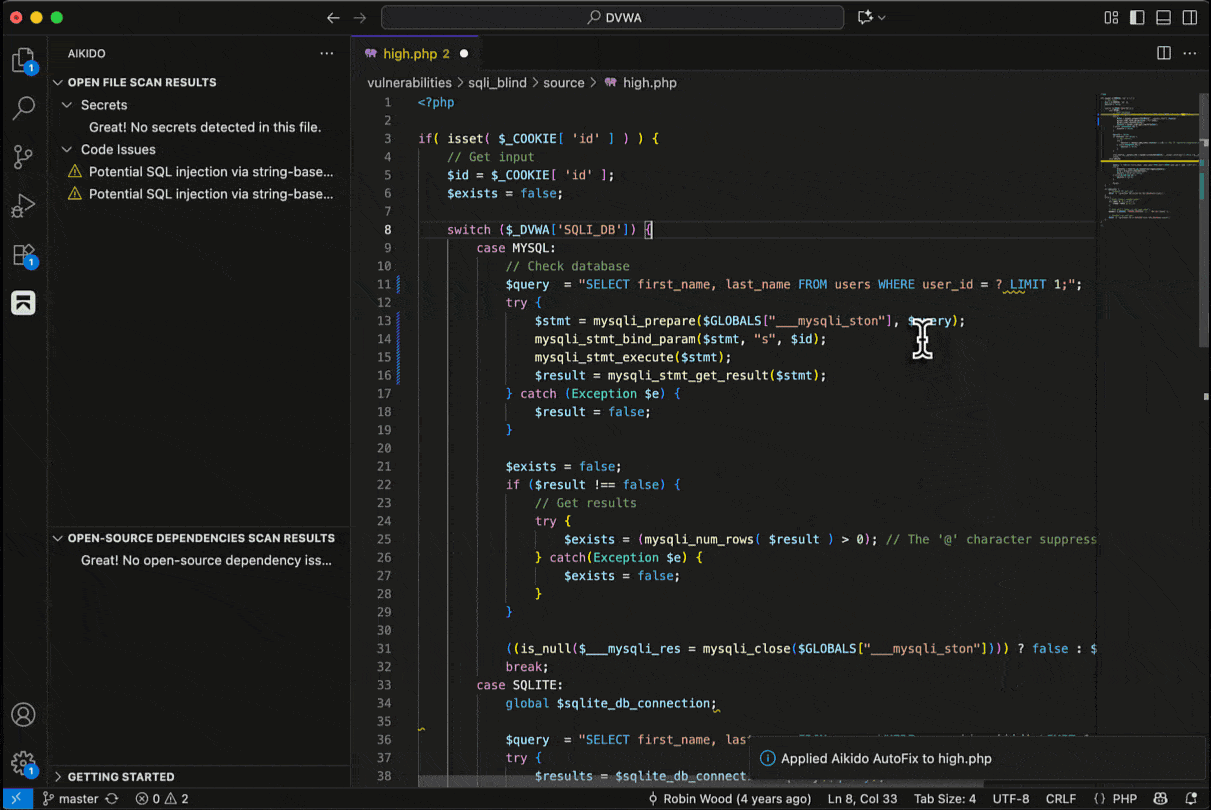
SCA AutoFix
How to test this extension
If this is your first time using this extension and you want to explore its capabilities, we suggest testing it with our example file below.
- Create a folder on your local machine.
- Open this folder in Visual Studio Code.
- Within this workspace, create a file containing the code you want to scan.
- Save the file.
- Any identified issues will appear as highlights in the editor and in the Problems panel below.
Below you can find an example index.js file that can be used to verify if the extension is working correctly, it should detect one SAST issue (SQL injection) and one exposed secret (SQL Server connection string).
const app = {}
app.get("/user", (req, res) => {
const connStr = "Server=tcp:myserver.database.windows.net,1433;Initial Catalog=mydb;Persist Security Info=False;User ID=myuser;Password=$uperSecret123!@#";
const username = req.query.username
const unsafeQuery = `SELECT * FROM users WHERE username = '${username}'`
sql.connect(connStr).query(unsafeQuery, (err, result) => {
res.status(200).send(result)
})
})
If you'd like to test Open-source dependency scanning you can add a sample package.json file with the following content:
{
"name": "demo-package-json",
"dependencies": {
"minimist": "1.2.5"
}
}
After this, run npm install or add a package-lock.json file with the following content:
{
"name": "demo-package-json",
"lockfileVersion": 3,
"requires": true,
"packages": {
"": {
"name": "demo-package-json",
"dependencies": {
"minimist": "1.2.5"
}
},
"node_modules/minimist": {
"version": "1.2.5",
"resolved": "https://registry.npmjs.org/minimist/-/minimist-1.2.5.tgz",
"integrity": "sha512-FM9nNUYrRBAELZQT3xeZQ7fmMOBg6nWNmJKTcgsJeaLstP/UODVpGsr5OhXhhXg6f+qtJ8uiZ+PUxkDWcgIXLw=="
}
}
}
Now, open the Open-source dependencies view in the Aikido side bar and click Start Scanning.
Commands
Execute Aikido extension commands through the Visual Studio Code Command Palette. The list below details some of the available commands. To see the full list, access the Command Palette by using Ctrl+⇧Shift+P or ⌘Command+⇧Shift+P (macOS).
Aikido: Log in: Enter an access token to connect with the Aikido Platform.Aikido: Reload rules: Fetches all SAST rules from the Aikido Platform. Useful when you add new custom rules.Aikido: Toggle showing ignored issues: Toggles the option to show/not show ignored issues. Useful when testing to show all issues that Aikido detects, even ones that are ignored.Aikido: Reload Rules: Reloads Aikido-defined and custom SAST rules into the extension.Aikido: Reload Aikido Vulnerabilities : Reloads SCA vulnerability definitions detected into the extension.
The integration does three types of scanning: secret, SAST and open-source dependency scanning. It uses Aikido-defined rules, supplemented by any custom rules you add to Aikido. The integration then processes any results to check for false positives or ignored issues. If you wish to see all the results, you can modify this behavior using the Toggle showing ignored issues command (see Commands section below).
How does the extension connect to Aikido
Using the access token that you provided, the extensions will connect and detect the matching repository in Aikido using the Git remote URL or the name of the project folder.




