Vault - Read KV secrets
Provide the ability to read KV secrets from HashiCorp Vault and load them into variables.
Note
The field « Secret path » have to ends with a « / » if you want to discover secrets across current folder and his subfolders.
See Use case 2.
In discovery mode if the « Prefix type » is set to « None » or « Custom » and you have secrets with the same name in different folder the last value read will be set in the variable (erasing previus values).
Examples
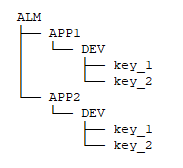
For the examples the following folder structure is created.
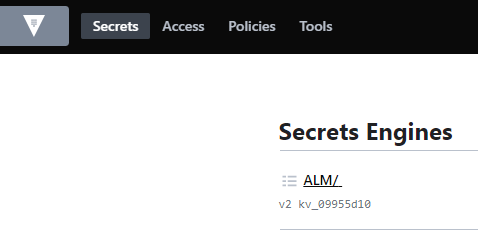
« ALM » is a KV v2 engine.
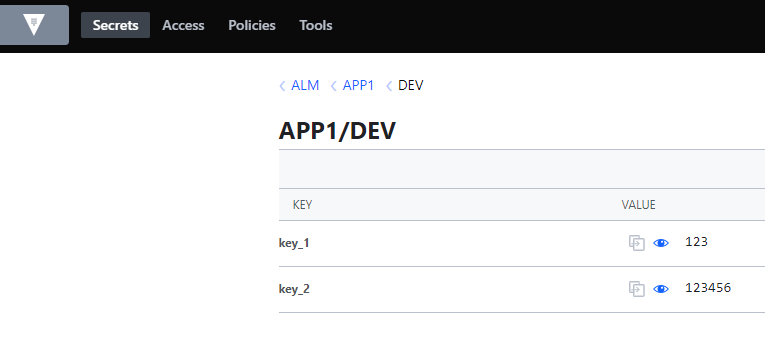
« APP1 » and « APP2 » is two folders containing a subfolder « DEV » and two secret « key_1 » and « key_2 ».
Use case 1
Read secrets from a KV v2 engine called « ALM » located at path « APP1/DEV ».
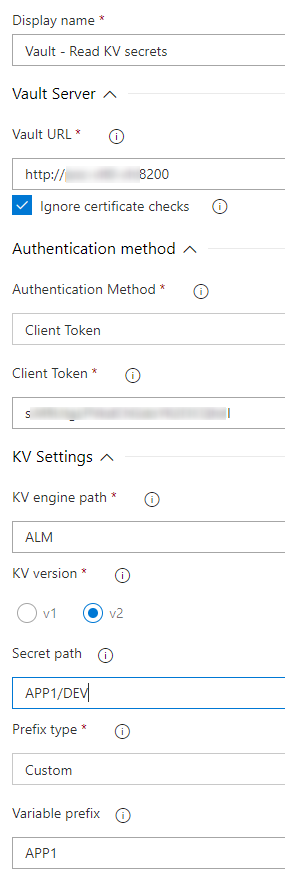
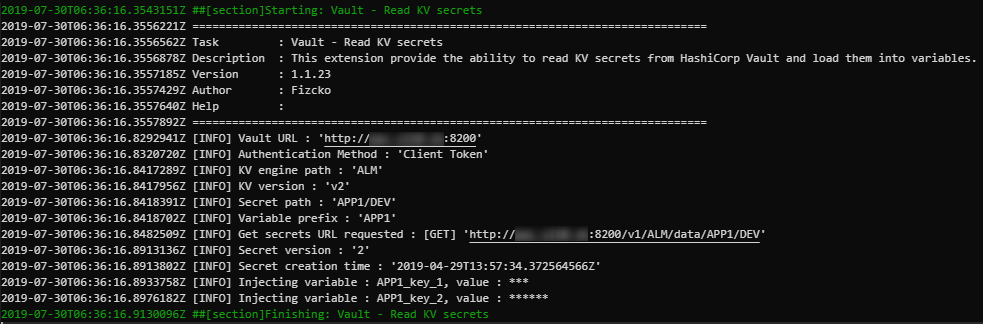
There is now two variables called « APP1_key_1 » and « APP1_key_2 » that you can used in your next tasks by using $(APP1_key_1) and/or $(APP1_key_2).
Use case 2
Read secrets from a KV v2 engine called « ALM » and browse recursively on sub folders.
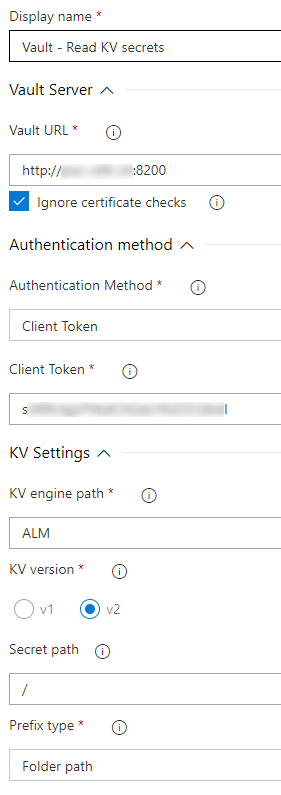
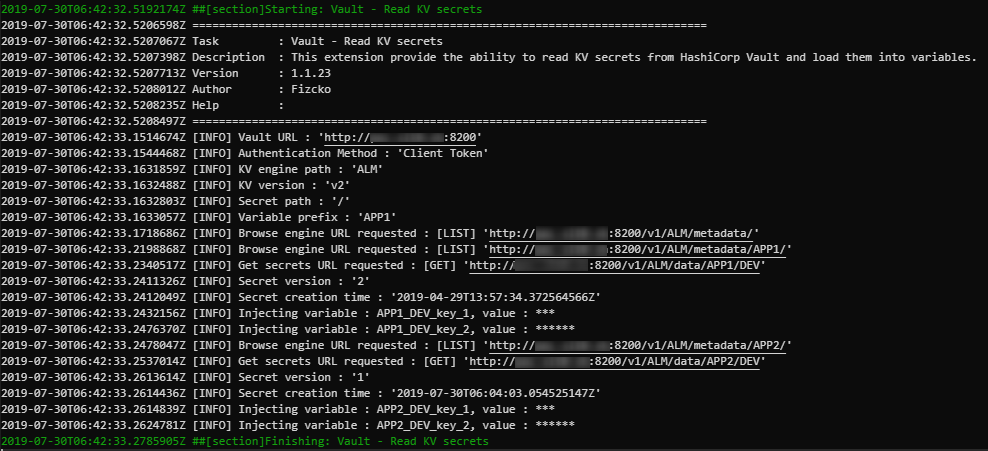
There is now four variables called « APP1_DEV_key_1 », « APP1_DEV_key_2 », « APP2_DEV_key_1 », « APP2_DEV_key_2 » that you can used in your next tasks by using $(APP1_DEV_key_1), $(APP1_DEV_key_2), $(APP2_DEV_key_1), $(APP2_DEV_key_2).