 finitestate.io
finitestate.io
Description
This extension adds three Finite State tasks to Azure DevOps pipelines:
- Analyze Binary
- Import SBOM (CycloneDX or SPDX)
- Import Third-Party Scan
These tasks upload artifacts to the Finite State Platform, create a project version when needed, and start the appropriate analysis or ingestion. The task output includes a direct link to the project version in the Finite State UI.
By default, the version’s release type is configurable. You can also choose to use the Azure Pipelines Build ID as the version by enabling “Use externalized ID as version.”
Task: Analyze Binary
Uploads a binary to Finite State and starts selected scans (e.g., SCA, SAST, Config, Vulnerability Analysis).
| parameter |
description |
required |
type |
default |
| subdomain |
Finite State subdomain (e.g., fs-yolo.dev.fstate.ninja) |
true |
string |
|
| apiToken |
API token |
true |
string |
|
| filePath |
File path to the binary to upload |
true |
filePath |
|
| scanTypes |
Scan types to run, comma/space/newline separated (e.g. sca,sast,config,vulnerability_analysis) |
true |
multiLine |
sca |
| projectName |
Project name |
true |
string |
|
| preRelease |
Mark version as PRE-RELEASE |
false |
boolean |
false |
| useExternalId |
Use pipeline Build ID as version |
false |
boolean |
true |
| projectVersion |
Explicit project version (required if useExternalId is false) |
false |
string |
|
| prComment |
Post a PR comment with a link to results (PR builds only) |
false |
boolean |
false |
Task: Import SBOM
Uploads an SBOM file for ingestion. Supports CycloneDX and SPDX formats.
| parameter |
description |
required |
type |
default |
| subdomain |
Finite State subdomain (e.g., fs-yolo.dev.fstate.ninja) |
true |
string |
|
| apiToken |
API token |
true |
string |
|
| filePath |
SBOM file path |
true |
filePath |
|
| sbomFormat |
SBOM format: cdx (cycloneDX) or spdx |
true |
string |
cdx |
| projectName |
Project name |
true |
string |
|
| preRelease |
Mark version as PRE-RELEASE |
false |
boolean |
false |
| useExternalId |
Use pipeline Build ID as version |
false |
boolean |
true |
| projectVersion |
Explicit project version (required if useExternalId is false) |
false |
string |
|
| prComment |
Post a PR comment with a link to results (PR builds only) |
false |
boolean |
false |
Task: Import Third-Party Scan
Uploads a third-party scan report to Finite State for ingestion.
| parameter |
description |
required |
type |
default |
| subdomain |
Finite State subdomain (e.g., fs-yolo.dev.fstate.ninja) |
true |
string |
|
| apiToken |
API token |
true |
string |
|
| filePath |
Scan file path |
true |
filePath |
|
| scanType |
Scan type identifier (e.g., zap_scan, snyk_scan). Must match one of the identifiers in the list below. |
true |
string |
|
| projectName |
Project name |
true |
string |
|
| preRelease |
Mark version as PRE-RELEASE |
false |
boolean |
false |
| useExternalId |
Use pipeline Build ID as version |
false |
boolean |
true |
| projectVersion |
Explicit project version (required if useExternalId is false) |
false |
string |
|
| prComment |
Post a PR comment with a link to results (PR builds only) |
false |
boolean |
false |
Note: For the scanType field, you must use one of the supported identifiers listed below. The value must match exactly to ensure the scan is recognized and processed correctly.
Third-Party scanType values (exact identifiers)
Click to expand/collapse the full list of supported scan types
| Tool |
scanType |
| Acunetix360 Scan |
acunetix360_scan |
| Acunetix Scan |
acunetix_scan |
| Anchore Engine Scan |
anchore_engine_scan |
| Anchore Enterprise Policy Check |
anchore_enterprise_policy_check |
| Anchore Grype |
anchore_grype |
| AnchoreCTL Policies Report |
anchorectl_policies_report |
| AnchoreCTL Vuln Report |
anchorectl_vuln_report |
| AppSpider Scan |
appspider_scan |
| Aqua Scan |
aqua_scan |
| Arachni Scan |
arachni_scan |
| AuditJS Scan |
auditjs_scan |
| AWS Prowler Scan |
aws_prowler_scan |
| AWS Prowler V3 |
aws_prowler_v3 |
| AWS Scout2 Scan |
aws_scout2_scan |
| AWS Security Finding Format (ASFF) Scan |
aws_security_finding_format_asff_scan |
| AWS Security Hub Scan |
aws_security_hub_scan |
| Azure Security Center Recommendations Scan |
azure_security_center_recommendations_scan |
| Bandit Scan |
bandit_scan |
| BlackDuck API |
blackduck_api |
| Blackduck Component Risk |
blackduck_component_risk |
| Blackduck Hub Scan |
blackduck_hub_scan |
| Brakeman Scan |
brakeman_scan |
| Bugcrowd API Import |
bugcrowd_api_import |
| BugCrowd Scan |
bugcrowd_scan |
| Bundler-Audit Scan |
bundler_audit_scan |
| Burp Enterprise Scan |
burp_enterprise_scan |
| Burp GraphQL API |
burp_graphql_api |
| Burp REST API |
burp_rest_api |
| Burp Scan |
burp_scan |
| CargoAudit Scan |
cargoaudit_scan |
| Checkmarx One Scan |
checkmarx_one_scan |
| Checkmarx OSA |
checkmarx_osa |
| Checkmarx Scan |
checkmarx_scan |
| Checkmarx Scan detailed |
checkmarx_scan_detailed |
| Checkov Scan |
checkov_scan |
| Clair Klar Scan |
clair_klar_scan |
| Clair Scan |
clair_scan |
| Cloudsploit Scan |
cloudsploit_scan |
| Cobalt.io API Import |
cobalt_io_api_import |
| Cobalt.io Scan |
cobalt_io_scan |
| Codechecker Report native |
codechecker_report_native |
| Contrast Scan |
contrast_scan |
| Coverity API |
coverity_api |
| Crashtest Security JSON File |
crashtest_security_json_file |
| Crashtest Security XML File |
crashtest_security_xml_file |
| CredScan Scan |
credscan_scan |
| CycloneDX |
cyclonedx |
| DawnScanner Scan |
dawnscanner_scan |
| Dependency Check Scan |
dependency_check_scan |
| Dependency Track Finding Packaging Format (FPF) Export |
dependency_track_finding_packaging_format_fpf_export |
| Detect-secrets Scan |
detect_secrets_scan |
| docker-bench-security Scan |
docker_bench_security_scan |
| Dockle Scan |
dockle_scan |
| DrHeader JSON Importer |
drheader_json_importer |
| DSOP Scan |
dsop_scan |
| Edgescan Scan |
edgescan_scan |
| ESLint Scan |
eslint_scan |
| Fortify Scan |
fortify_scan |
| Generic Findings Import |
generic_findings_import |
| Ggshield Scan |
ggshield_scan |
| Github Vulnerability Scan |
github_vulnerability_scan |
| GitLab API Fuzzing Report Scan |
gitlab_api_fuzzing_report_scan |
| GitLab Container Scan |
gitlab_container_scan |
| GitLab DAST Report |
gitlab_dast_report |
| GitLab Dependency Scanning Report |
gitlab_dependency_scanning_report |
| GitLab SAST Report |
gitlab_sast_report |
| GitLab Secret Detection Report |
gitlab_secret_detection_report |
| Gitleaks Scan |
gitleaks_scan |
| Gosec Scanner |
gosec_scanner |
| Govulncheck Scanner |
govulncheck_scanner |
| HackerOne Cases |
hackerone_cases |
| Hadolint Dockerfile check |
hadolint_dockerfile_check |
| Harbor Vulnerability Scan |
harbor_vulnerability_scan |
| Horusec Scan |
horusec_scan |
| HuskyCI Report |
huskyci_report |
| Hydra Scan |
hydra_scan |
| IBM DAST |
ibm_appscan_dast |
| Immuniweb Scan |
immuniweb_scan |
| IntSights Report |
intsights_report |
| JFrog Xray API |
jfrog_xray_api_summary_artifact_scan |
| JFrog Xray Scan |
jfrog_xray_scan |
| JFrog Xray Unified Scan |
jfrog_xray_unified_scan |
| KICS Scan |
kics_scan |
| Kiuwan Scan |
kiuwan_scan |
| Kube Bench Scan |
kube_bench_scan |
| Logic Bomb |
logic_bomb |
| Meterian Scan |
meterian_scan |
| Microfocus WebInspect Scan |
microfocus_webinspect_scan |
| MobSF Scan |
mobsf_scan |
| Mobsfscan Scan |
mobsfscan_scan |
| Mozilla Observatory Scan |
mozilla_observatory_scan |
| Netsparker Scan |
netsparker_scan |
| NeuVector (compliance) |
neuvector_compliance |
| NeuVector (REST) |
neuvector_rest |
| Nexpose Scan |
nexpose_scan |
| Nikto Scan |
nikto_scan |
| Nmap Scan |
nmap_scan |
| Node Security Platform Scan |
node_security_platform_scan |
| NPM Audit Scan |
npm_audit_scan |
| Nuclei Scan |
nuclei_scan |
| Openscap Vulnerability Scan |
openscap_vulnerability_scan |
| OpenVAS CSV |
openvas_csv |
| ORT evaluated model Importer |
ort_evaluated_model_importer |
| OssIndex Devaudit SCA Scan Importer |
ossindex_devaudit_sca_scan_importer |
| Outpost24 Scan |
outpost24_scan |
| PHP Security Audit v2 |
php_security_audit_v2 |
| PHP Symfony Security Check |
php_symfony_security_check |
| pip-audit Scan |
pip_audit_scan |
| PMD Scan |
pmd_scan |
| Popeye Scan |
popeye_scan |
| PWN SAST |
pwn_sast |
| Qualys Infrastructure Scan (WebGUI XML) |
qualys_infrastructure_scan_webgui_xml |
| Qualys Scan |
qualys_scan |
| Qualys Webapp Scan |
qualys_webapp_scan |
| Retire.js Scan |
retire_js_scan |
| Rubocop Scan |
rubocop_scan |
| Rusty Hog Scan |
rusty_hog_scan |
| SARIF |
sarif |
| Scantist Scan |
scantist_scan |
| Scout Suite Scan |
scout_suite_scan |
| Semgrep JSON Report |
semgrep_json_report |
| SKF Scan |
skf_scan |
| Snyk Scan |
snyk_scan |
| Solar Appscreener Scan |
solar_appscreener_scan |
| SonarQube Cloud Scan |
sonarqube_cloud_scan |
| SonarQube Scan |
sonarqube_scan |
| SonarQube Scan detailed |
sonarqube_scan_detailed |
| Sonatype Application Scan |
sonatype_application_scan |
| SPDX |
spdx |
| SpotBugs Scan |
spotbugs_scan |
| SSL Labs Scan |
ssl_labs_scan |
| Sslscan |
sslscan |
| SSLyze Scan (JSON) |
sslyze_scan_json |
| Sslyze Scan |
sslyze_scan |
| StackHawk HawkScan |
stackhawk_hawkscan |
| Talisman Scan |
talisman_scan |
| Tenable Scan |
tenable_scan |
| Terrascan Scan |
terrascan_scan |
| Testssl Scan |
testssl_scan |
| TFSec Scan |
tfsec_scan |
| Trivy Operator Scan |
trivy_operator_scan |
| Trivy Scan |
trivy_scan |
| Trufflehog3 Scan |
trufflehog3_scan |
| Trufflehog Scan |
trufflehog_scan |
| Trustwave Fusion API Scan |
trustwave_fusion_api_scan |
| Trustwave Scan (CSV) |
trustwave_scan_csv |
| Twistlock Image Scan |
twistlock_image_scan |
| VCG Scan |
vcg_scan |
| Veracode Scan |
veracode_scan |
| Veracode SourceClear Scan |
veracode_sourceclear_scan |
| Vulners |
vulners |
| Wapiti Scan |
wapiti_scan |
| Wazuh |
wazuh |
| WFuzz JSON report |
wfuzz_json_report |
| Whispers Scan |
whispers_scan |
| WhiteHat Sentinel |
whitehat_sentinel |
| Whitesource Scan |
whitesource_scan |
| Wpscan |
wpscan |
| Xanitizer Scan |
xanitizer_scan |
| Yarn Audit Scan |
yarn_audit_scan |
| ZAP Scan |
zap_scan |
Set Up Workflow
To start using this Extension, install it from the Azure DevOps Marketplace.
After it is installed, you can add the Finite State tasks to your pipeline by finding them in the Tasks panel:
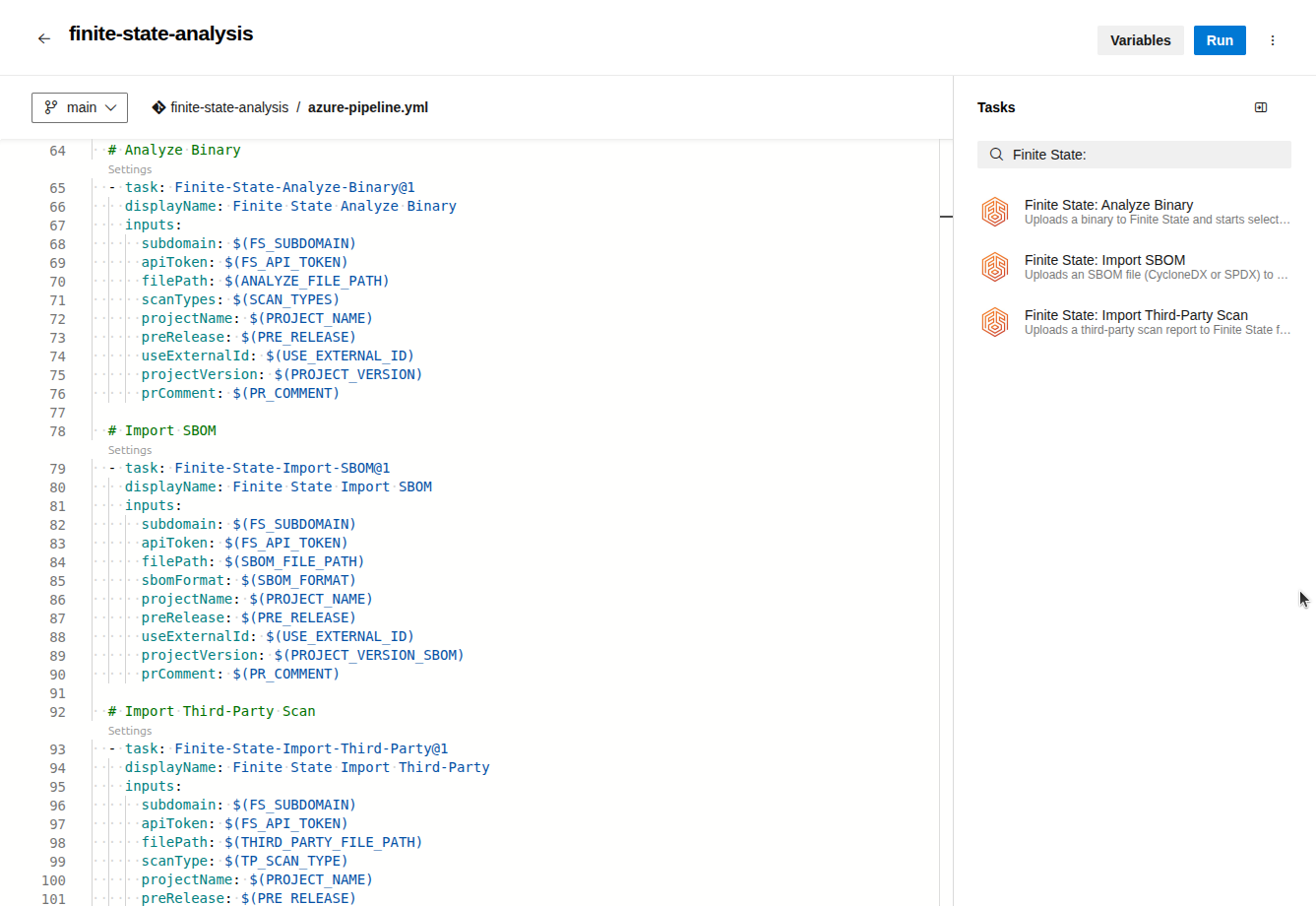
You can customize the input parameters for each task:
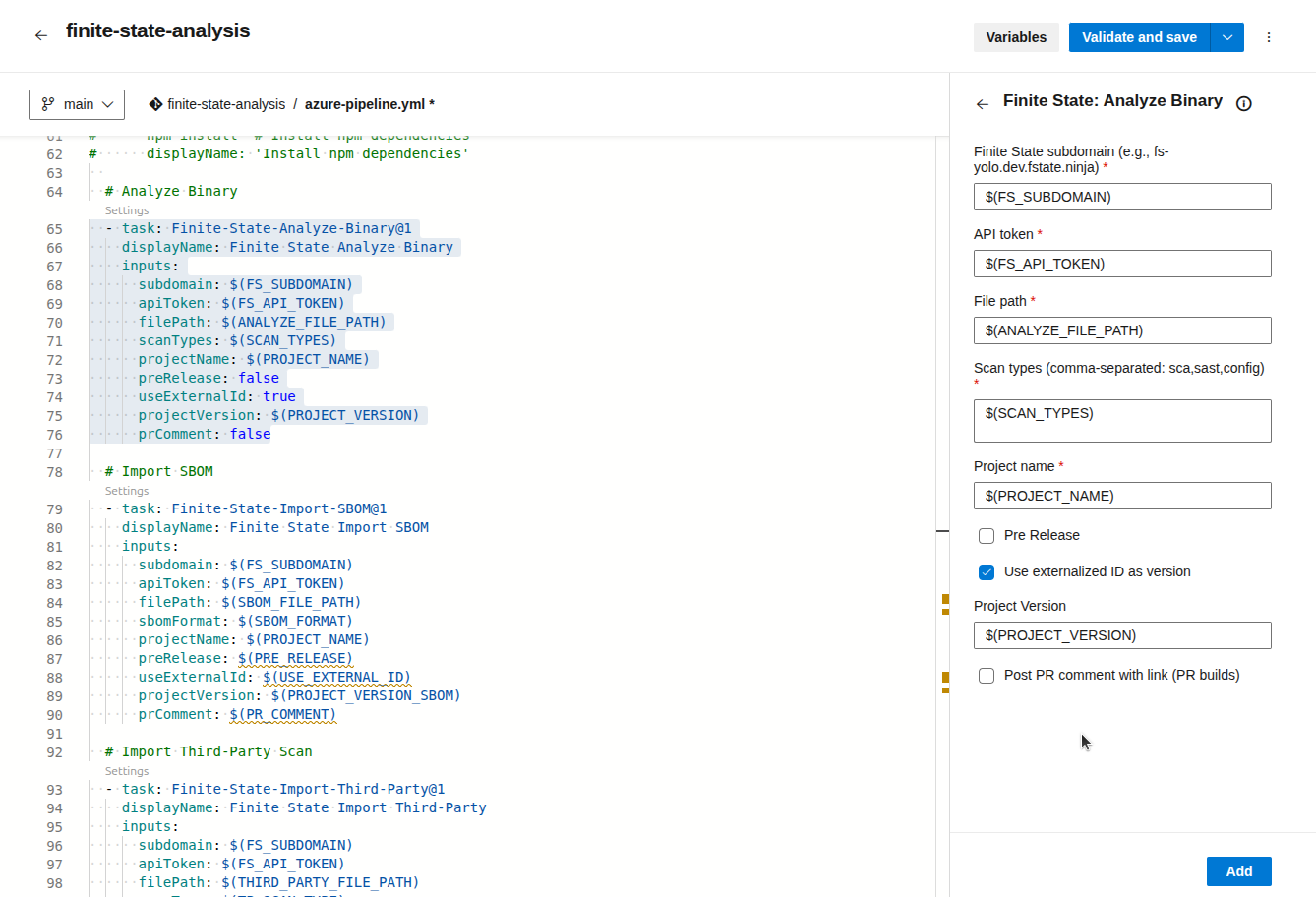
Although you can write values directly in the input fields, we recommend storing sensitive values as secrets rather than hardcoding them in the pipeline YAML. At minimum, store the following as secrets:
- API token (obtained from the Finite State platform at Settings → API Tokens)
When you run the pipeline, the task logs will include a link to the created project version in the Finite State UI.
If you want the tasks to automatically generate a PR comment with a link to the results on the Finite State Platform, make sure to give permissions to the Azure pipeline token System.AccessToken. Then, grant the necessary permissions to the associated token by going to Project Settings > Repositories > Security:
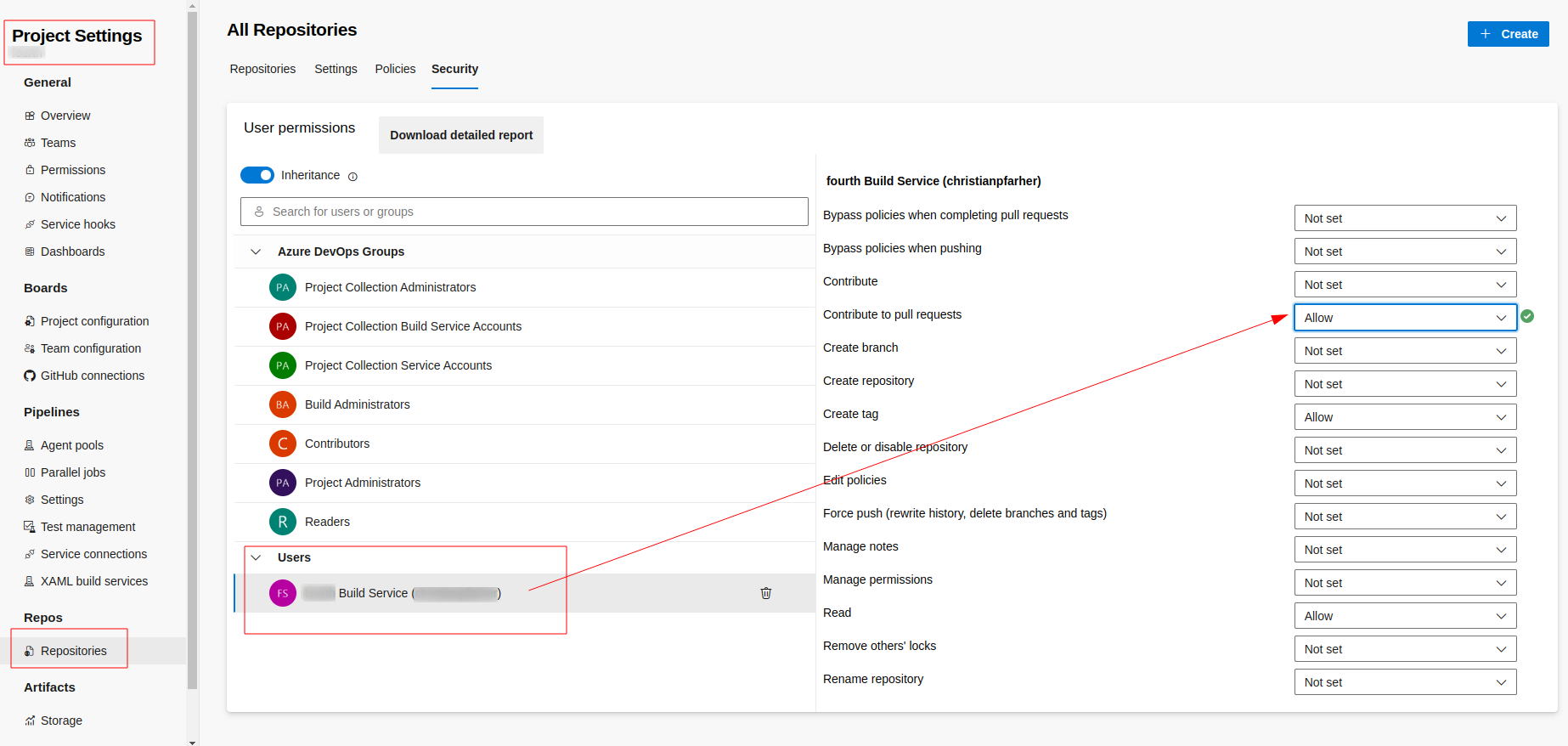
This allows the task to post a comment in the PR when prComment is enabled (true). After this step, you will get a comment in the PR with a link that points to the results in the Finite State Platform:
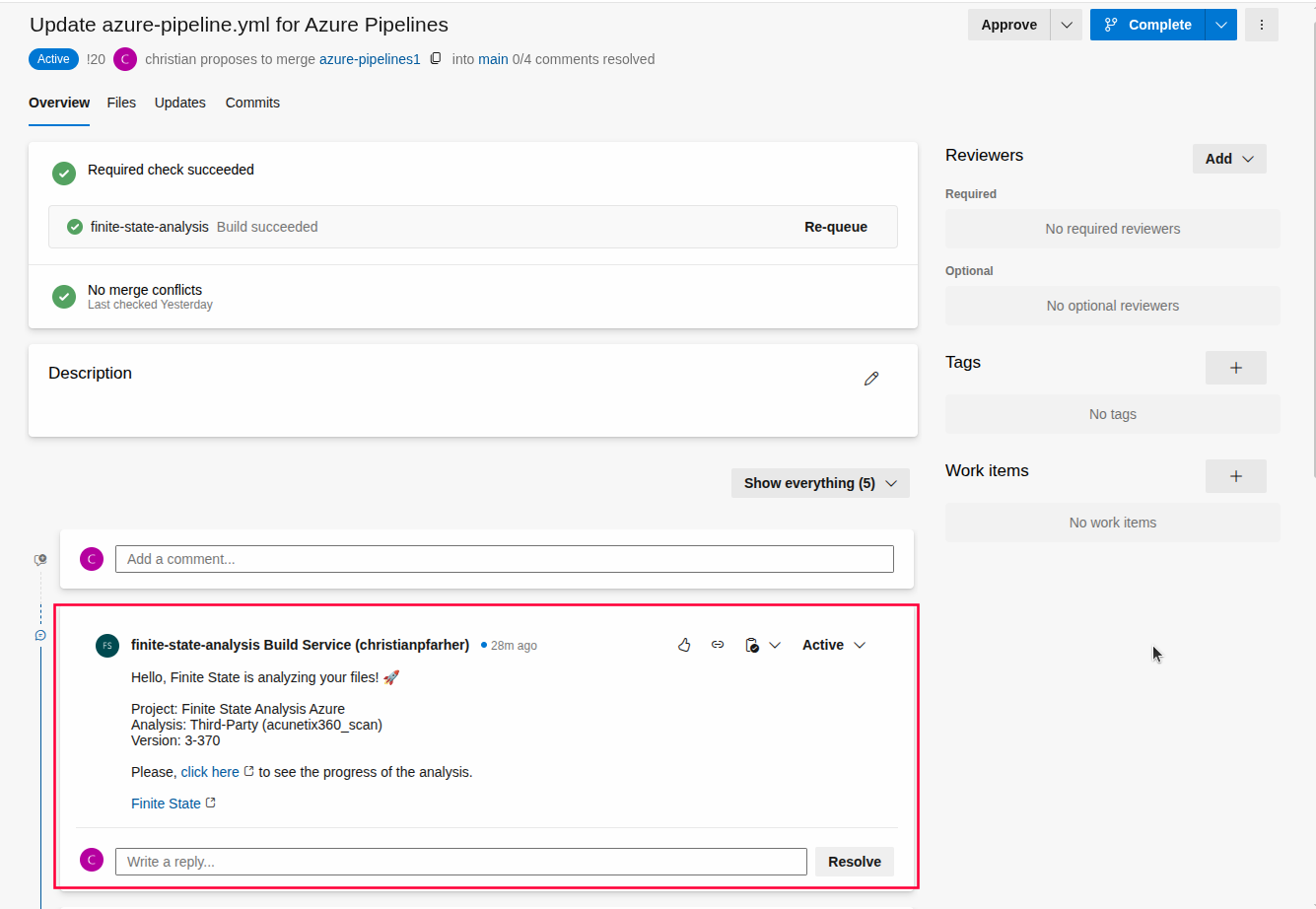
Build Policy
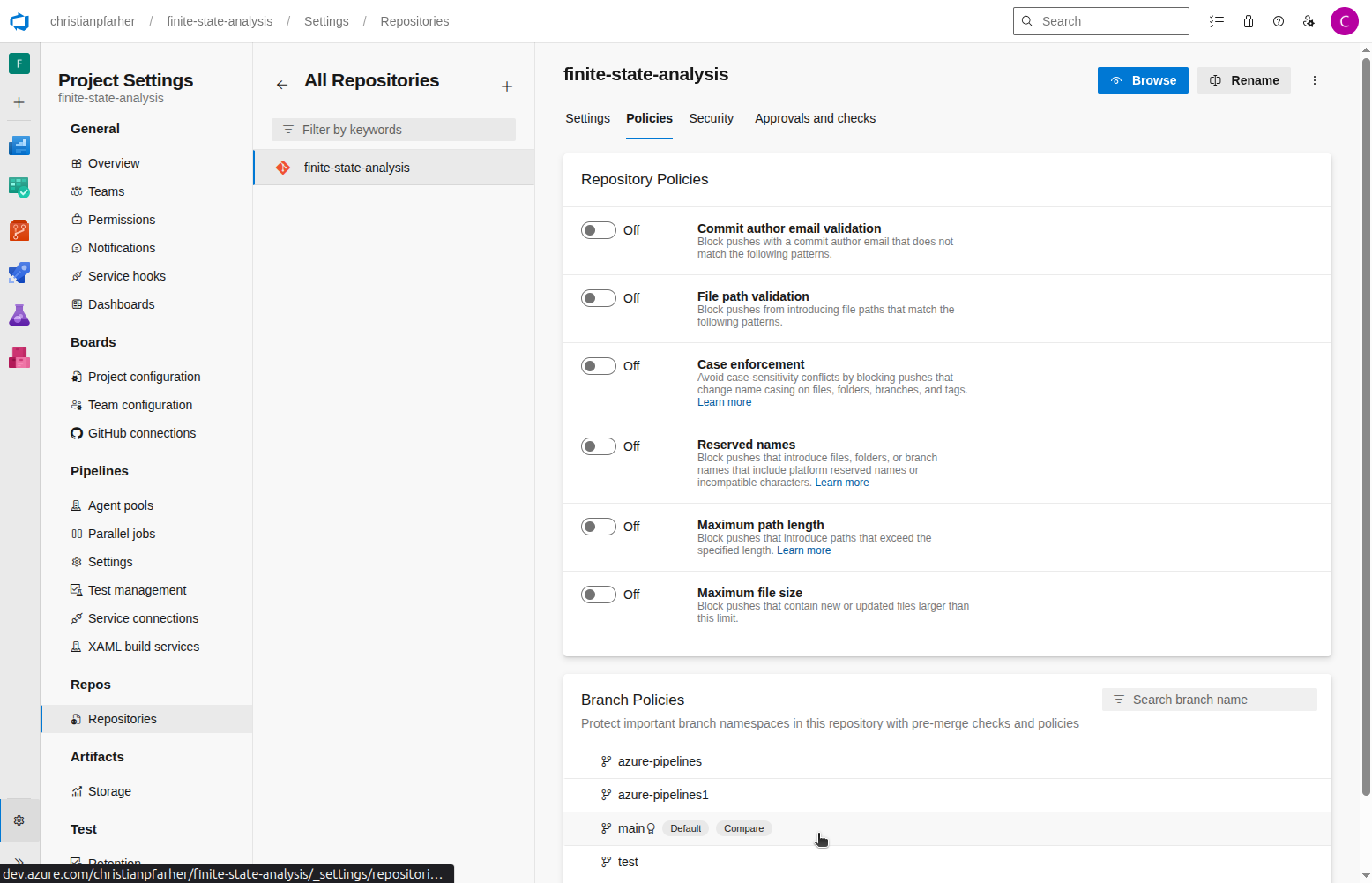
Configure a build policy over your main branch to automatically start a build when a PR targets it. This ensures each commit to a PR branch triggers the pipeline and, if configured, posts a PR comment.
To set up a policy, go to Project Settings > Repositories > [Select the repository] > Policies Tab. In the Branch Policies section, click on main branch:
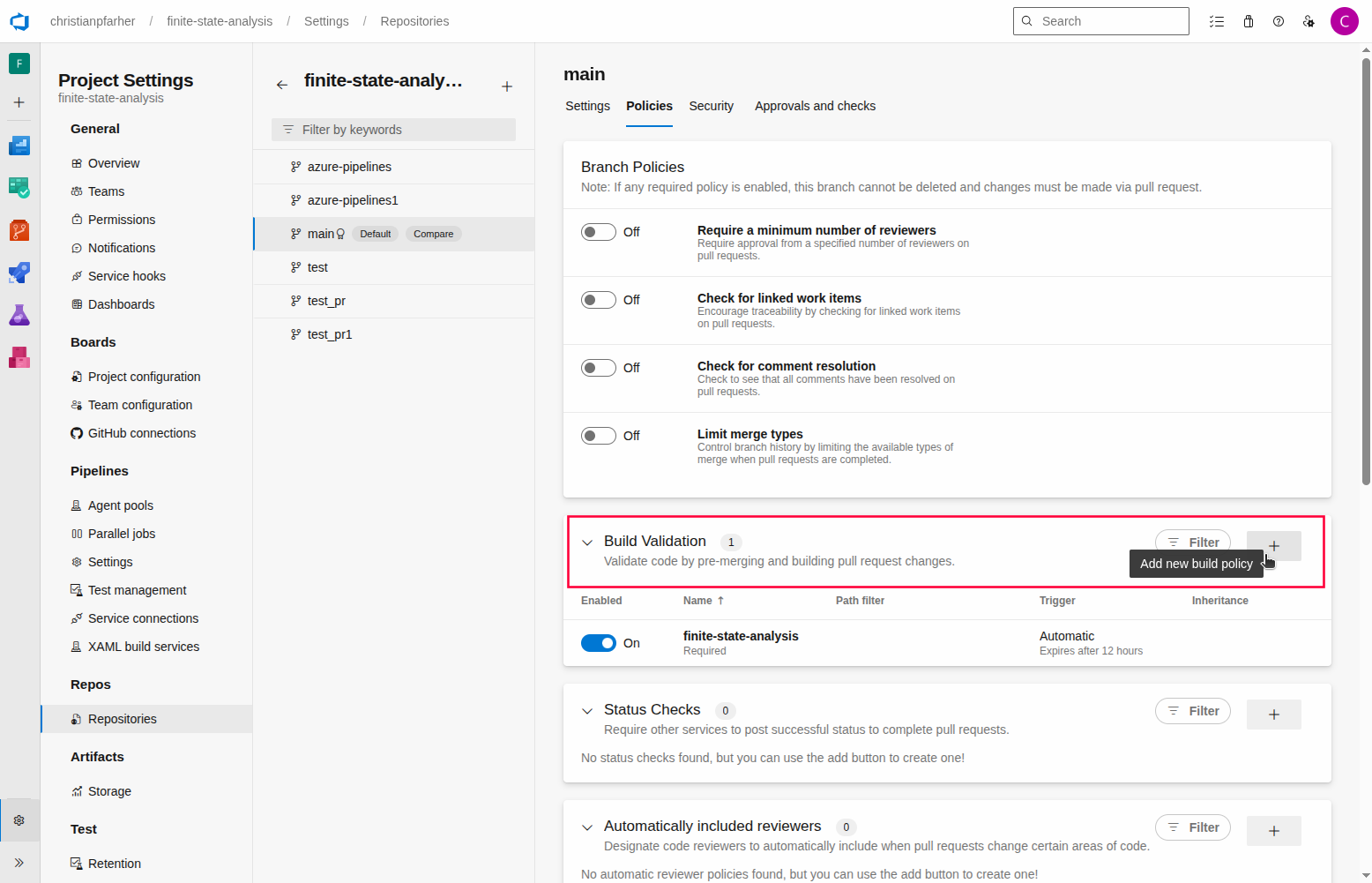
On the Build Validation section, add a new build policy:
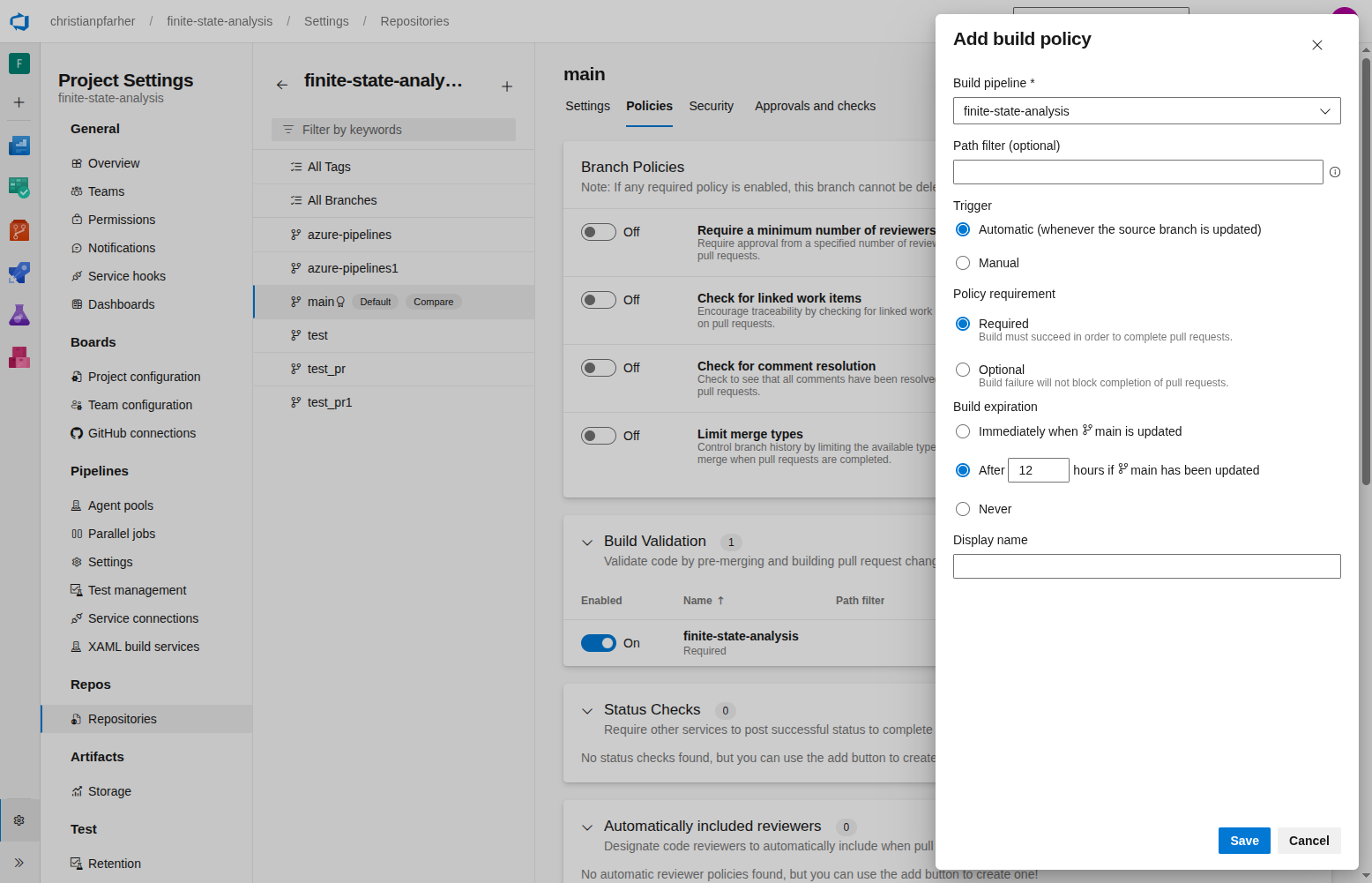
In the dialog, save the settings as follows:
After that, you will see a configuration similar to this:
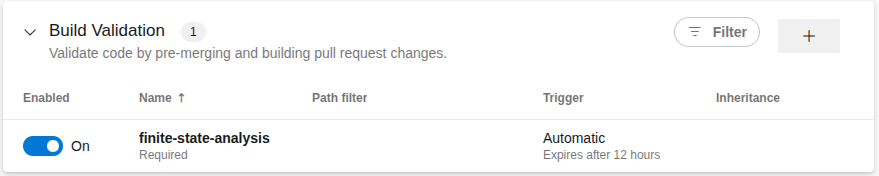
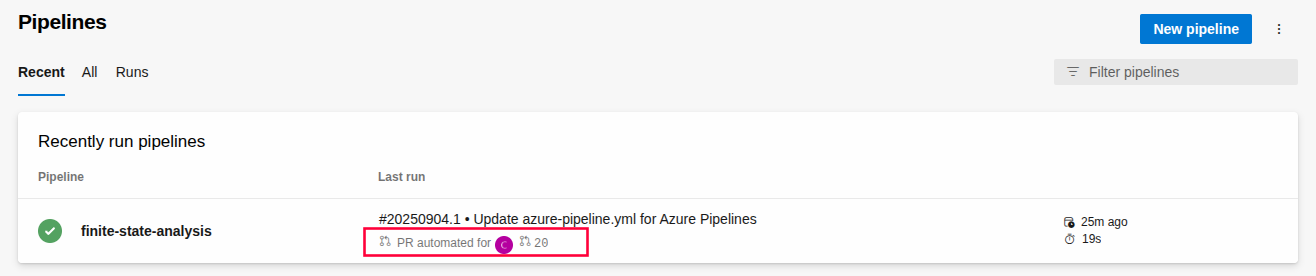
Going forward, each commit to a branch associated with a PR targeting the main branch will trigger the pipeline automatically and execute the Finite State task:
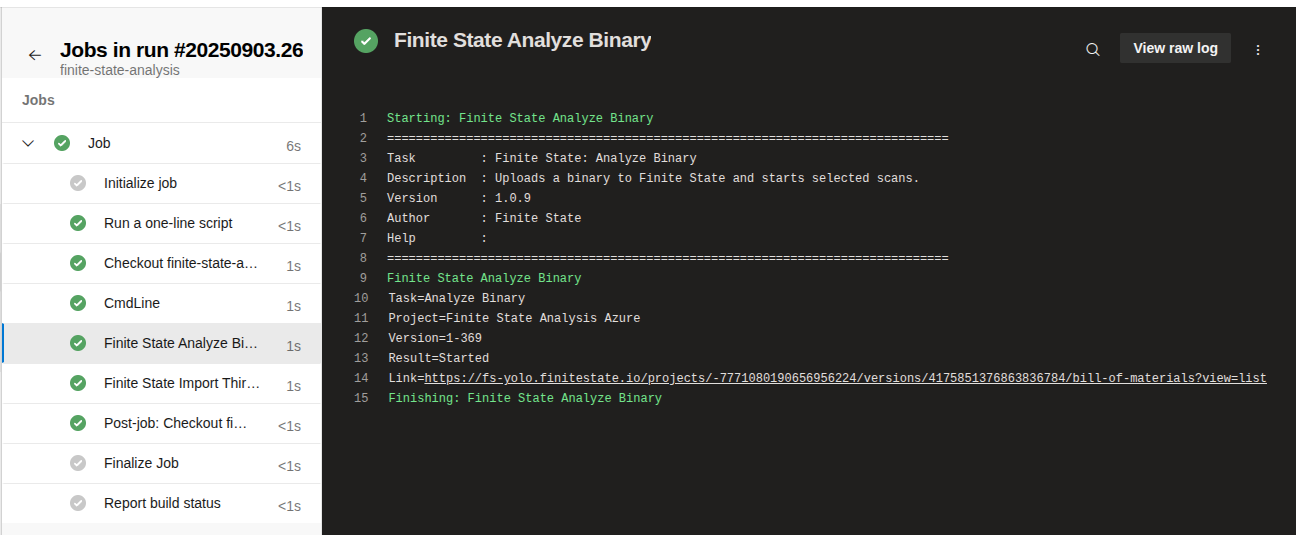
The task logs will summarize the execution and include links to the created project version:
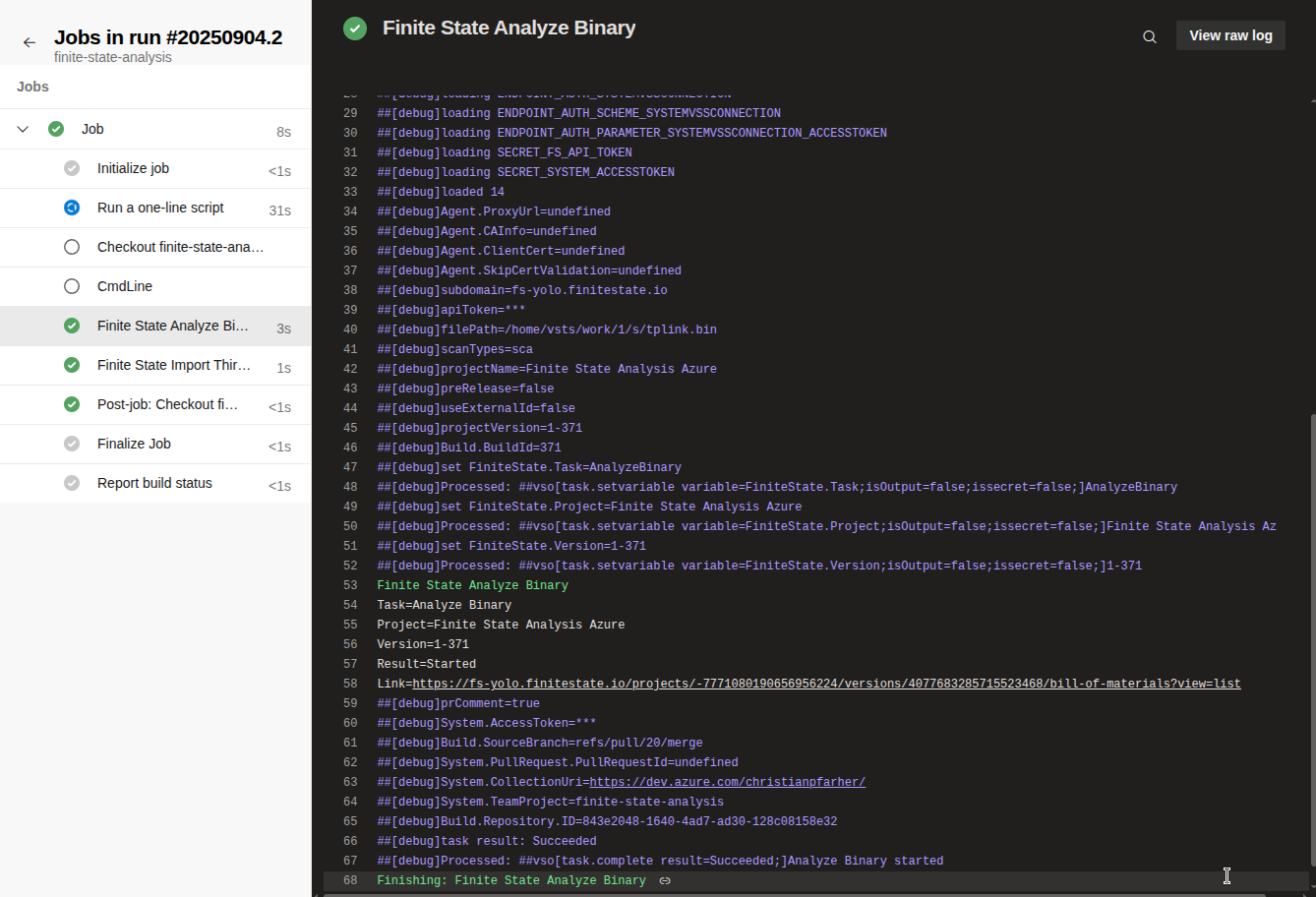
Action Debugging
All details pertaining to the execution of the tasks are recorded in the workflow logs. This is a helpful starting point if you encounter any errors during a run.
If you have any errors, enable System diagnostics when you run the pipeline to capture verbose logs:
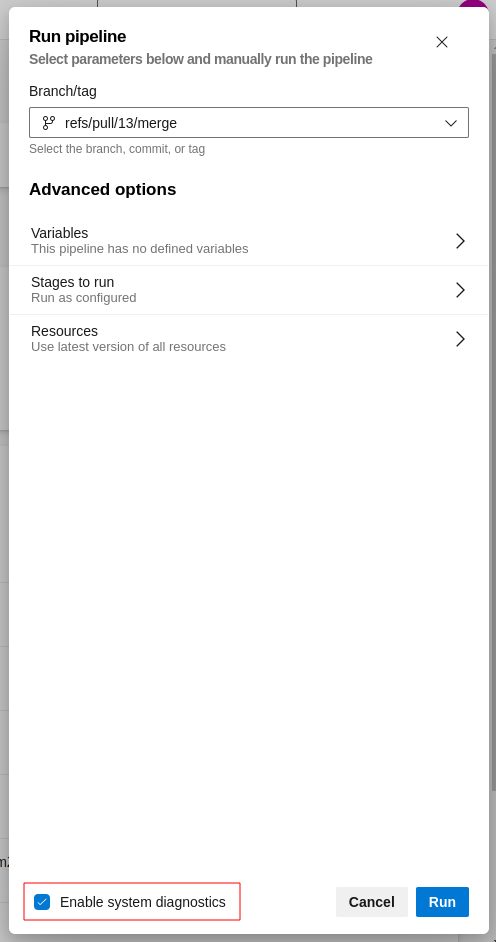
Example output when System diagnostics is enabled:
Useful Links















